What is Get-ADGroupMember cmdlet
The Get-ADGroupMember cmdlet is used to get of members of an Active Directory group.
In this post, we will show you how to use Get-ADGroupMember cmdlet to get the list of members and how to export them to CSV.
How to Use Get-ADGroupMember cmdlet
You can just type the Get-ADGroupMember cmdlet in a PowerShell window and you’ll be prompted to enter the name of the group you want to use.
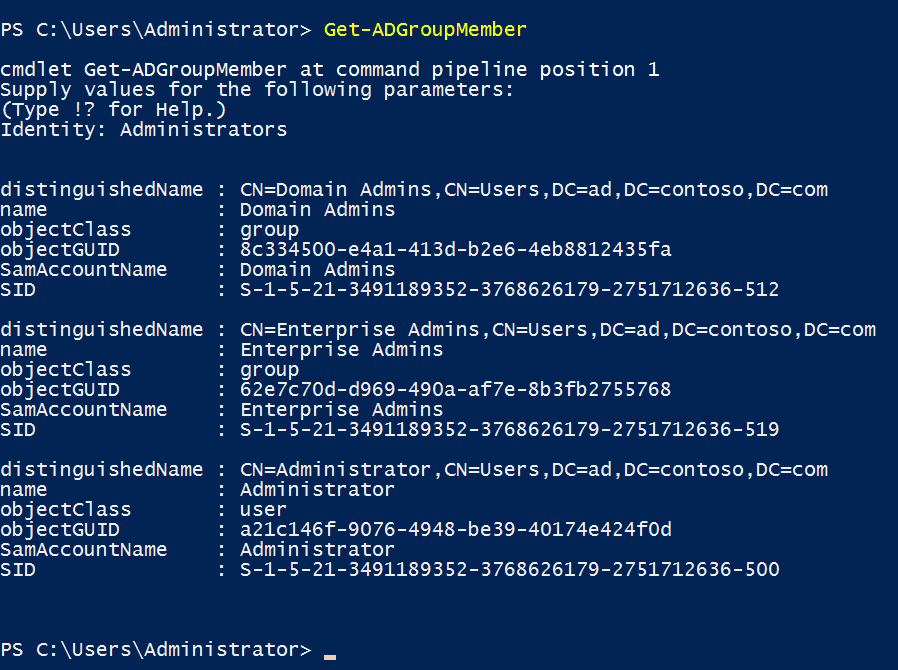
Note that you must be logged in to Windows with a domain user account that has permission to read the group(s) you want to list. You must also have the Active Directory module for Windows PowerShell installed on the device where you want to run the Get-ADGroupMember cmdlet.
You can add the name of the group to the command as shown below and format the output by piping the results to the Select-Object cmdlet:
Get-ADGroupMember -Identity Administrators | Select-Object name, objectClass,distinguishedNameCombine the Get-ADGroup and Get-ADGroupMember cmdlets to perform more complex searches. In the example below, I list all members of groups with domain local scope:
Get-ADGroup -Filter {GroupScope -eq "DomainLocal"} | Get-ADGroupMember | Select-Object name, objectClass,distinguishedName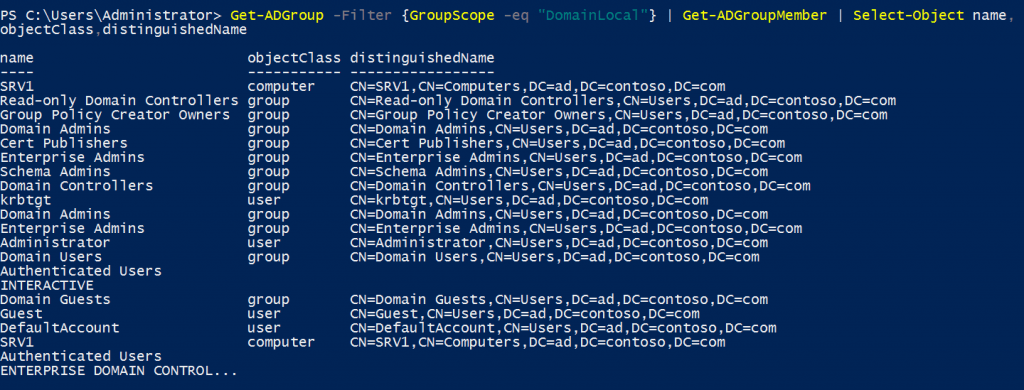
You can add the -Recursive parameter to Get-ADGroupMember to list all members of child groups.
Get-ADGroupMember -Identity 'Enterprise Admins' -RecursiveNote that the group name is enclosed using apostrophes because it contains a space. Don’t forget that Out-GridView can be useful for sorting and filtering the results using a simple GUI interface.
Get-ADGroupMember -Identity Administrators | Select-Object name, objectClass,distinguishedName | Out-GridViewExport List of Active Directory Group Members to CSV
If you want a keepsake or want to perform further processing, you can export the list to a comma-delimited file that can be opened in Excel or used by another program. The command below saves the group members list to the current working directory in a file called adgroupmembers.csv.
Get-ADGroupMember -Identity Administrators | Select-Object name, objectClass,distinguishedName | Export-CSV -Path “adgroupmembers.csv”Get-ADGroupMember Parameters
Below is the list of Get-ADGroupMember parameters:
- -AuthType
- -Credential
- -Identity
- -Partition
- -Recursive
- -Server
-AuthType
This specifies the authentication method to use. The acceptable values for this parameter are:
- Negotiate or 0
- Basic or 1
- A distinguished name
- A GUID (objectGUID)
- A security identifier (objectSid)
- A Security Account Manager account name (sAMAccountName)
- If the Identity parameter is set to a distinguished name, the default value of Partition is automatically generated from this distinguished name.
- If running cmdlets from an Active Directory provider drive, the default value of Partition is automatically generated from the current path in the drive.
- If none of the previous cases apply, the default value of Partition is set to the default partition or naming context of the target domain.
- If the Identity parameter is set to a distinguished name, the default value of Partition is automatically generated from this distinguished name.
- If running cmdlets from an Active Directory provider drive, the default value of Partition is automatically generated from the current path in the drive.
- If the target AD LDS instance has a default naming context, the default value of Partition is set to the default naming context. To specify a default naming context for an AD LDS environment, set the msDS-defaultNamingContext property of the Active Directory directory service agent object (nTDSDSA) for the AD LDS instance.
- If none of the previous cases apply, the Partition parameter does not take a default value.
- Fully qualified domain name
- NetBIOS name
- Fully qualified directory server name
- NetBIOS name
- Fully qualified directory server name and port
- By using the Server value from objects passed through the pipeline
- By using the server information associated with the AD DS Windows PowerShell provider drive, when the cmdlet runs in that drive
- By using the domain of the computer running Windows PowerShell
The default authentication method is Negotiate.
A Secure Sockets Layer (SSL) connection is required for the Basic authentication method.
-Credential
This specifies the user account credentials to use to perform this task. The default credentials are the credentials of the currently logged on user unless the cmdlet is run from an Active Directory module for Windows PowerShell provider drive. If the cmdlet is run from such a provider drive, the account associated with the drive is the default.
To specify this parameter, you can type a user name, such as User1 or Domain01\User01 or you can specify a PSCredential object. If you specify a user name for this parameter, the cmdlet prompts for a password.
You can also create a PSCredential object by using a script or by using the Get-Credential cmdlet. You can then set the Credential parameter to the PSCredential object.
If the acting credentials do not have directory-level permission to perform the task, Active Directory module for Windows PowerShell returns a terminating error.
-Identity
This specifies an Active Directory group object by providing one of the following values. The identifier in parentheses is the LDAP display name for the attribute. The acceptable values for this parameter are:
The cmdlet searches the default naming context or partition to find the object. If two or more objects are found, the cmdlet returns a non-terminating error.
This parameter can also get this object through the pipeline or you can set this parameter to an object instance.
-Partition
Specifies the distinguished name of an Active Directory partition. The distinguished name must be one of the naming contexts on the current directory server. The cmdlet searches this partition to find the object defined by the Identity parameter.
In many cases, a default value is used for the Partition parameter if no value is specified. The rules for determining the default value are given below. Note that rules listed first are evaluated first and once a default value can be determined, no further rules are evaluated.
In Active Directory Domain Services (AD DS) environments, a default value for Partition is set in the following cases:
In Active Directory Lightweight Directory Services (AD LDS) environments, a default value for Partition is set in the following cases:
-Recursive
Specifies that the cmdlet get all members in the hierarchy of a group that do not contain child objects.
If the specified group does not have any members, then nothing is returned.
-Server
Specifies the AD DS instance to connect to, by providing one of the following values for a corresponding domain name or directory server. The service may be any of the following: AD LDS, AD DS, or Active Directory snapshot instance.
Specify the AD DS instance in one of the following ways:
Domain name values:
Directory server values:
The default value for this parameter is determined by one of the following methods in the order that they are listed:
How Lepide Auditor Helps
This method of exporting group members using PowerShell is time-consuming and requires a good knowledge of PowerShell scripting. In addition, the results returned using this method are in a format that’s very hard to read and difficult to analyze.
A more straightforward approach is to use the Lepide Auditor for Active Directory. The List All Group Members Report can be used to show all members of Active Directory groups:
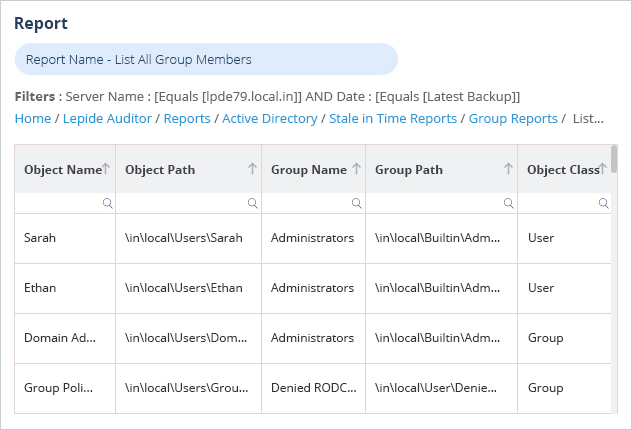
To run this report:
- Click the User & Entity Behavior Analytics icon and select the List all Group Members Report from the Active Directory Reports
- Click Generate Report to run the report
- The report can be filtered to report on a particular Group Name and can be grouped to list all members by their group
- The report can be saved and exported to CSV, PDF or MHT format

