As an IT administrator, it’s important to know the location that users are logging in from. When users are logging on to Azure Active Directory (Azure AD) outside of trusted locations, it needs to be monitored as it could be indicative of an attack.
Azure AD Conditional Access policies enable you to control user access to resources to help keep your organization secure. However, these days, with so many more remote workers and cloud applications, your attack surface is significantly larger, and so it is crucial to keep track of Azure AD sign-in events.
The Azure (AD) audit logs record all logon events, but you cannot easily filter the entries to exclude trusted locations, leaving you with a large volume of information to process manually.
A more straightforward solution to this is to use the Lepide Azure AD Auditor. This enables you to generate reports on both successful and failed attempts to logon to Azure AD. Trusted locations can be filtered out to display only the information you are looking for providing an efficient way to monitor Azure AD logons.
Here are two ways to detect logons outside of trusted locations in Azure AD and they are described below.
- Audit Logons Outside of Trusted Locations Using Native Auditing
- Audit Logons Outside of Trusted Locations Using Lepide
Audit Logons Outside of Trusted Locations Using Native Auditing
Please follow the below steps to audit outside logons:
- Open portal.azure.com
- Click Azure Active Directory
- Click Sign-in logs from the Monitoring section
- Click Download, CSV
- Import the resulting file into Microsoft Excel
From Excel:
- Click File, Open and select the file you previously downloaded
From the Text Import Wizard:
- Choose Data Type = Delimited
- Check the My data has headers box
- Click Next
From the Delimiters section:
- Check Comma
- Click Next
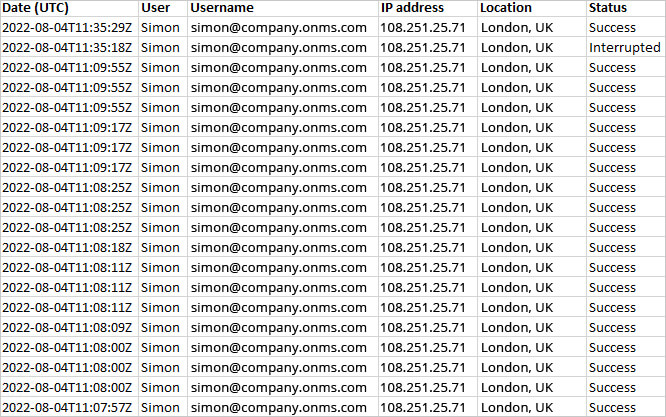
- Scroll through the fields preview and choose Do not import column (skip), leaving only the following columns: Date (UTC), User, Username, IP address, Location, Status.
- Click Finish
- Apply an Excel filter to filter by trusted locations or IP addresses using the Location or IP address column.
Note: For more logon details, you can also leave the Application, Resource, Authentication requirement, and Browser, Operating System fields checked
Audit Azure AD Logons Outside of Trusted Locations Using Lepide
This native way to track Logons outside of Trusted Locations in Azure AD is both time-consuming and complex and requires using both Azure AD and Excel to generate a report. A more straightforward solution to this is to use the Lepide Azure AD Auditor.
Lepide Azure AD Auditor overcomes the complexity of the native method by providing a straightforward way to list all logons outside of trusted locations in Azure AD using the All Modifications in Azure AD Report:
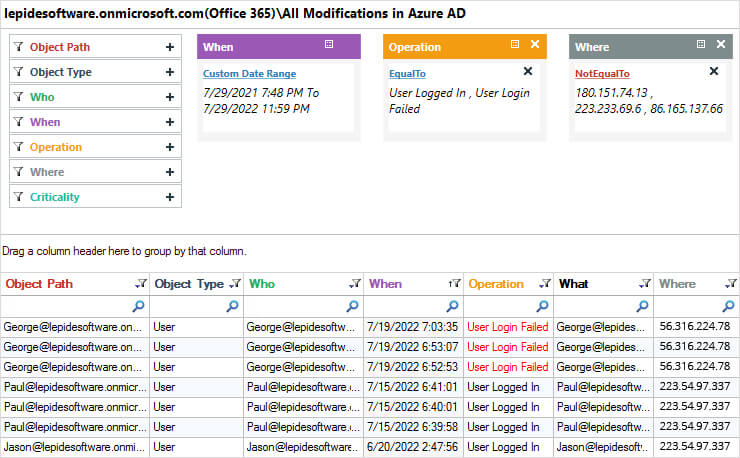
- To see all users who have tried to log in:
Filter by Operation and select User Logged in and User Login Failed
- To exclude all trusted locations and show only logins outside of trusted locations:
Filter by Where, change the filter criteria to Not Equal to and add all trusted locations
- Click Generate Report
The report will list all logins, whether successful or failed, from outside of trusted locations for the time period specified.
Conclusion
In conclusion, you can see that Lepide Azure AD Auditor provides a straightforward way to report on Azure AD login activity resulting in a comprehensive yet clear to understand report.

