One of the most challenging tasks Administrators face on a daily basis is managing Active Directory user accounts. It is particularly important to monitor who and why changes are being made to ensure that they are valid.
Why it’s Important to Track Disabled User Accounts in Active Directory
Active Directory configuration changes need to be carefully monitored so that users have access to all the resources they require. If a user’s account becomes disabled, they will not have access to essential system functions including email, files and SharePoint which will disrupt business operations.
Another reason to ensure that disabled users are tracked in Active Directory is to reduce the risk of a data breach. Disabled accounts represent a serious threat as they can be re-enabled and misused by attackers seeking access to Active Directory, Windows servers and other AD-integrated systems. Therefore, it is crucial to have visibility over who disabled a user account to establish the reason for doing this.
In this article, we will discuss the steps you need to take to detect who disabled a user account in Active Directory. We will first look at doing this using native auditing, followed by a more straightforward approach using the Lepide Auditor for Active Directory.
Find Who Disabled a User Account using Event Logs (Event ID 4725)
Please follow the below steps:
- Run gpmc.msc to open the Group Policy Management Console.
- Create a new GPO and Edit it
- Go to Computer Configuration, Policies, Windows Settings, Security Settings, Local Policies > Audit Policy:
- Double click Audit Account Management Policy, Define, Success.
- Click Apply and OK
- Go to Event Log, Define:
- Maximum security log size to 4GB
- Retention method for security log to Overwrite events as needed.
- Link the new GPO to the OU with User Accounts: Go to Group Policy Management, Right-click the defined OU, choose Link an Existing GPO, Choose the GPO that you’ve created.
- Force the group policy update, In Group Policy Management, Right-click the defined OU, Click on Group Policy Update.
- Full Control
- List Contents
- Read all properties
- Read permissions, Click OK.
- Open ADSI Edit, Connect to Default naming context, Right-click DomainDNS object with the name of your domain, Properties, Security (Tab), Advanced (Button), Auditing (Tab), Add Principal Everyone, Type Success, Applies to This object and Descendant objects, Permissions, Select all check boxes except the following:
- Open Event viewer and search Security log for event ID’s 4725 (User Account Management task category).
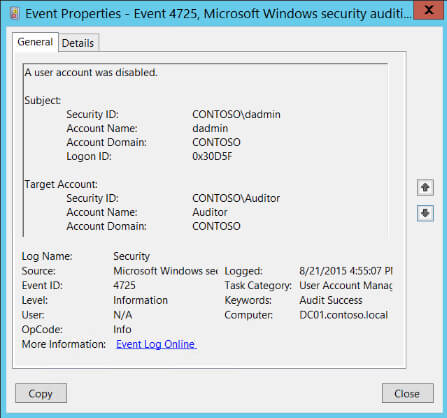
Note: This event only generates on domain controllers and member servers.
How Lepide Auditor Helps
A quicker and more straightforward way to identify who has disabled a user is to use Lepide Auditor for Active Directory. Our Active Directory auditing software can provide you with in-depth visibility with real-time alerts that help you overcome the limitations of native auditing.
The following is an example of the User Status Modifications report, one of many pre-defined reports included the Lepide Auditor:
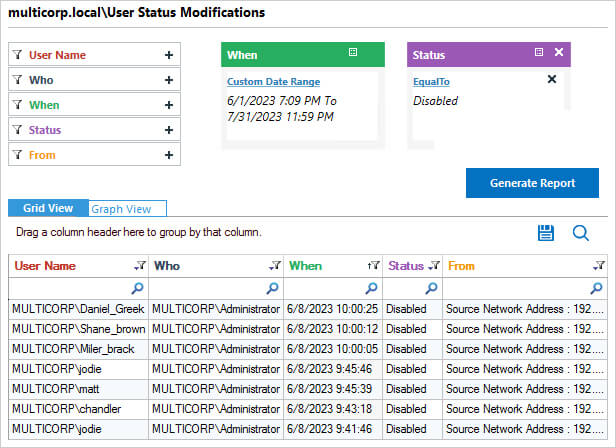
The report includes information showing the User Name of the account which has been disabled together with Who has disabled it.
To run the report:
- From the States & Behavior window, choose Active Directory Reports and select User Status Modifications
- Specify a date range, select Disabled from the Status filter and click Generate Report

