Having visibility over user activity in your critical systems is a crucial part of identifying potential suspicious behavior which may lead to security breaches. Tracking user activity provides the necessary information to spot malicious activity and stop an organization falling victim to a potential cyberattack.
The auditing of logon events in Active Directory (AD) is a mandatory task to help with the detection of malicious activity. Any anomaly in the audit report will help to detect security risks in multiple ways; for example, an employee’s account becoming locked out after multiple logon failures is a potential threat to a company’s data security.
A login failure could just be an employee who has forgotten their credentials. However, in a different scenario, it could be a hacker trying to enter the network through an employee’s legitimate account. So, any failed login attempt needs to be monitored to mitigate any security risk.
Logon activity can be monitored using native Active Directory auditing tools, but it is a time consuming and often complex task. The Lepide Auditor for Active Directory overcomes the limitations of native auditing by giving you the visibility you need to detect and react to insider threats quickly and efficiently.
In this article, we will look at two methods for tracking failed logon attempts: the native method and a more straightforward solution using the Lepide Auditor.
Please follow below steps to track source of Failed Logon Attempts using Event Logs
Step 1. Enable Auditing for Logon Failure
- Logon to your domain controller with administrative privileges and launch the Group Policy Management console
- Right-click the appropriate Group Policy Object linked to the Domain Controllers container and select Edit
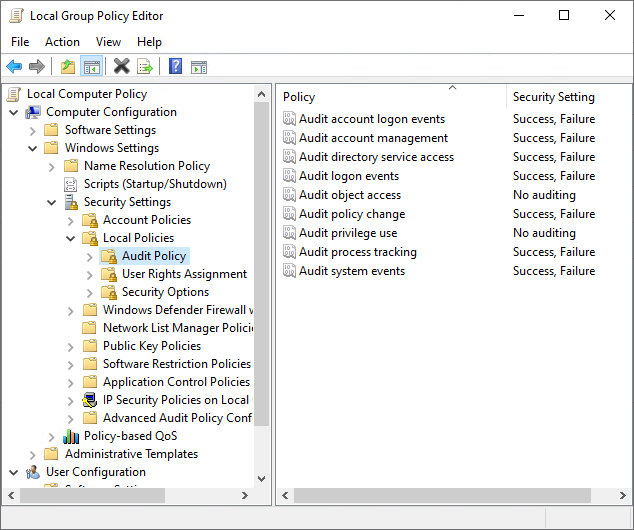
- Expand Computer Configuration, Windows Setting, Security Settings, Local Policies, Audit Policy node
- Configure audit policies as follows:
Account Management: Success
Audit account logon events: Failure
Audit logon events: Failure
Step 2. Search Event ID 4625 to Find Failed Logon Attempts Source
Once auditing is enabled, you can use the Event Viewer to see the logs and review events.
Follow the steps below to view and filter event logs:
- Open Event Viewer
- Expand Windows Logs, Security
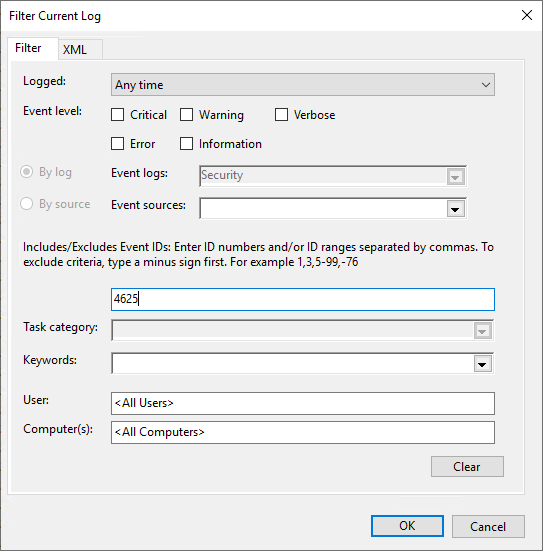
- Filter the events to show Event ID 4625 which is the Event for login failure.
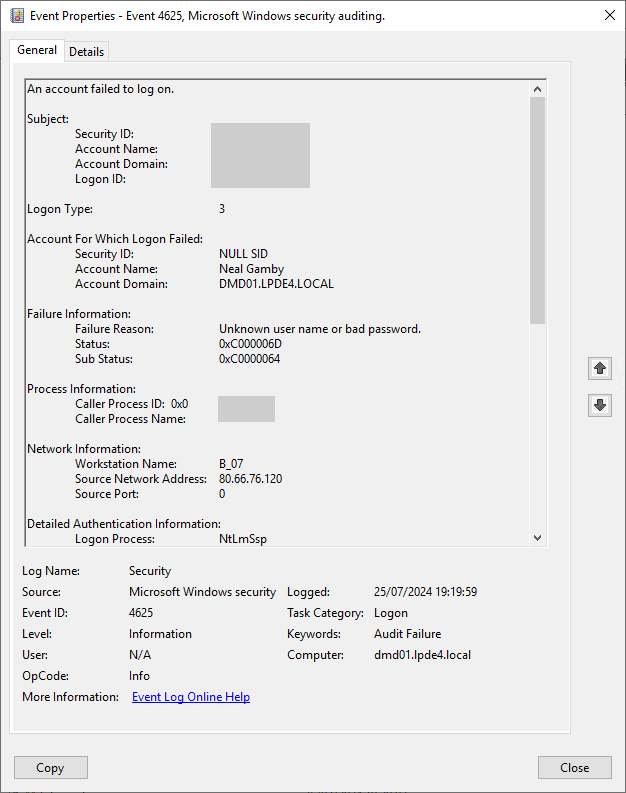
- Once filtered, double click on an event. You can view detailed information about the activity such as account name, date and time of login failure as in the example below:
How Lepide Auditor Can Help
As you can see, this native way to find files with sensitive data is both time consuming and complex. A more straightforward solution to this is to use Lepide Auditor for Active Directory which includes many pre-defined reports including the Failed Logons Report. An example of this report is shown as follows:
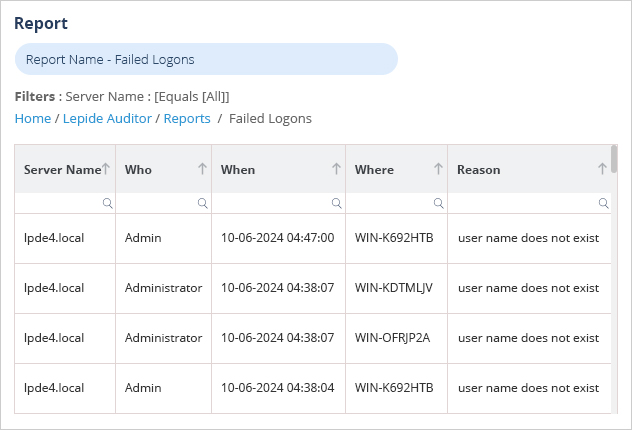
To run the Failed Logons Report:
- Select Lepide Auditor, Reports. From this screen, expand Active Directory and select Failed Logons
- Specify a date range
- Select Generate Report
- The report is generated and can be filtered, sorted and exported to CSV and PDF format

