Monitoring your employees’ logon activity is a crucial step in identifying and preventing any unwanted activity taking place on your network.
The tracking of users’ logon events can help detect unusual logon patterns such as logons occurring at unusual times, logons to unauthorized hosts, and any other suspicious activities. It also helps administrators identify and respond to sudden spikes in failed logon attempts, as this could indicate the possibility of a brute force attack.
The tracking of users’ logon events can help detect unusual logon patterns such as logons occurring at unusual times, logons to unauthorized hosts, and any other suspicious activities. It also helps administrators identify and respond to sudden spikes in failed logon attempts, as this could indicate the possibility of a brute force attack.
Enabling Account Logon Events Auditing
The Event Viewer is a native tool provided by Microsoft which allows you to view event logs including logon activity events. Before you can use the Event Viewer, your domain’s audit policy needs to be enabled. The steps to do this are as follows:
- Open the Group Policy Management Console or run the command gpmc.msc
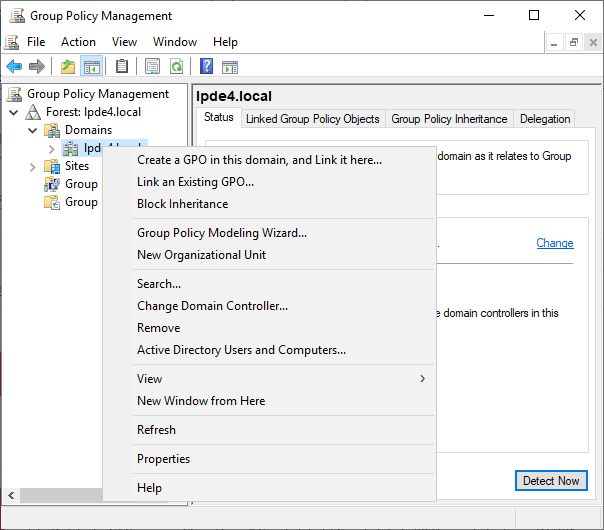
- To audit accounts in a specific Organizational Unit (OU), right click on that Organizational Unit and click on Create a GPO in this domain, and Link it here
- Name the Group Policy Object (GPO)
- Right click on the newly created GPO and choose Edit
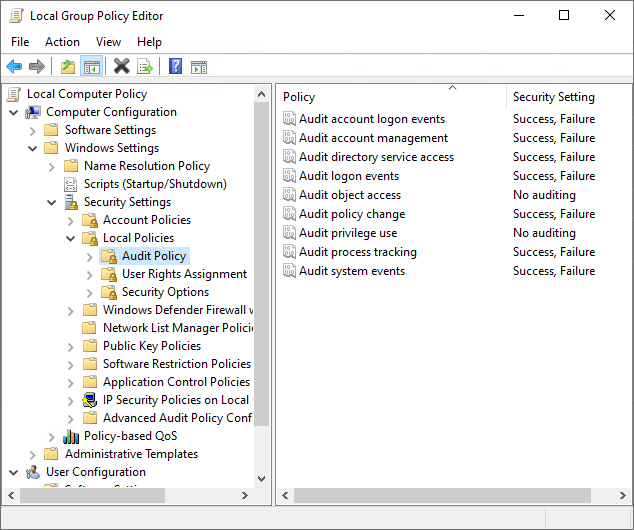
- In the Group Policy Management Editor, on the left pane, navigate to Computer Configuration, Policies, Windows Settings, Security Settings, Local Policies, Audit Policy
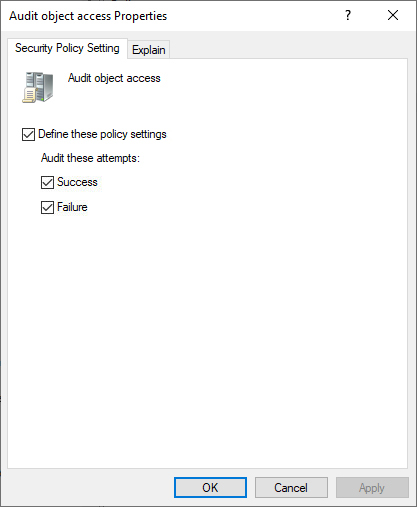
- In the right pane, you will see a list of policies for Audit Policy. Double-click Audit account logon events and check the boxes labeled Define these policy settings, Success, and Failure
- Click on Apply and then on OK
- Go back to the Group Policy Management Console, and on the left pane, right click on the OU or domain in which the GPO was linked and click on Group Policy Update. This step makes sure the new Group Policy settings are applied instantly instead of waiting for the next scheduled refresh
- Once this policy is enabled, events are logged on to the Domain Controller (DC) security log whenever a logon is validated by the Domain Controller
To audit all the accounts in the domain, right click on the domain name and click on Create a GPO in this domain, and Link it here
Find Account Logon Events in Event Viewer
Once the above steps are complete, account logon events are recorded as event logs using various Event IDs. These events can be viewed in the Event Viewer by following the steps below:
- Open Event Viewer
- On the left pane of the Event Viewer, navigate to Windows log, Security
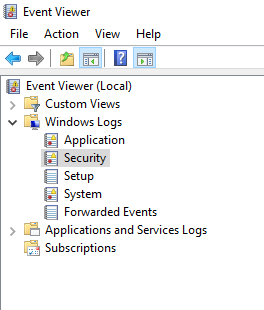
- Here, you will find a list of all the security events that are logged
- On the right pane, under security, click on Filter current log
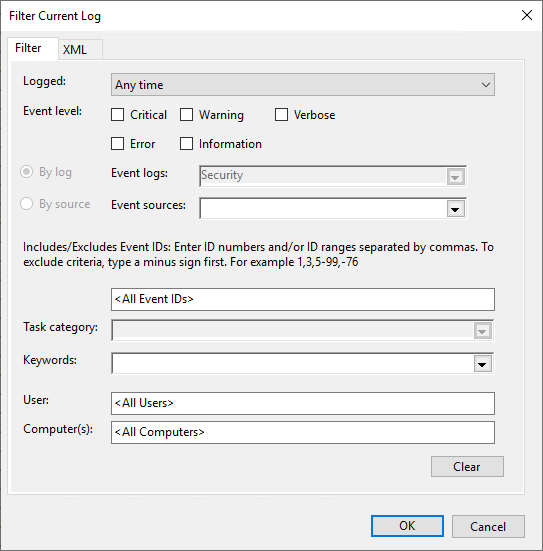
- In the pop-up window, enter the required Event ID
- By default, only successful logon attempts are audited. Failed attempts can be audited by enabling it in Advanced Audit Policy Configuration as described above
- Click on OK
- Double-click on the Event ID to view its properties
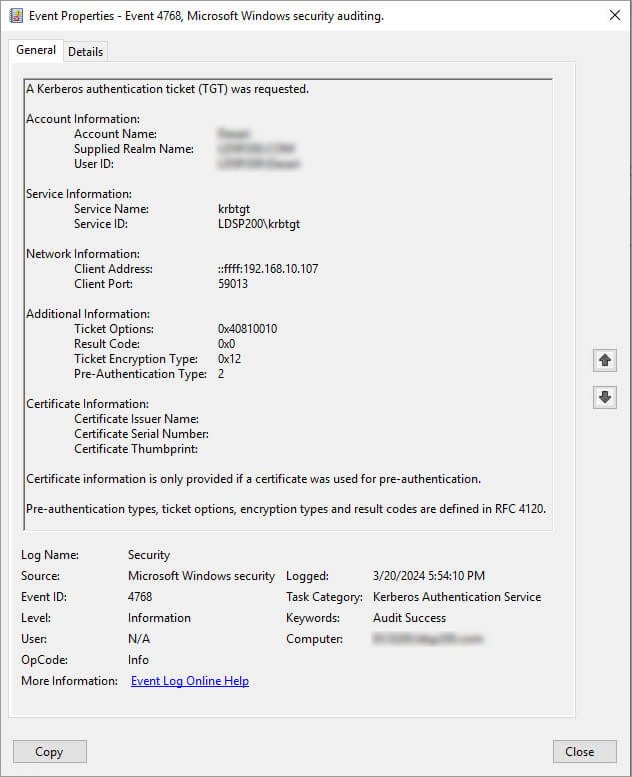
The following Event IDs are generated for the Success and Failure events:
How Lepide can Help
As you can see, getting an overview of all logon events on your network is a tedious task using native auditing. An administrator would have to search for the Event ID and view each event’s properties which is highly impractical.
A more straightforward solution to using the Event Viewer to track logon events is to use the Lepide Auditor for Active Directory. The Lepide Solution includes many pre-defined reports to monitor Active Directory activity and one example of these is the Domain Controller Logon/Logoff’s Report which is shown below:
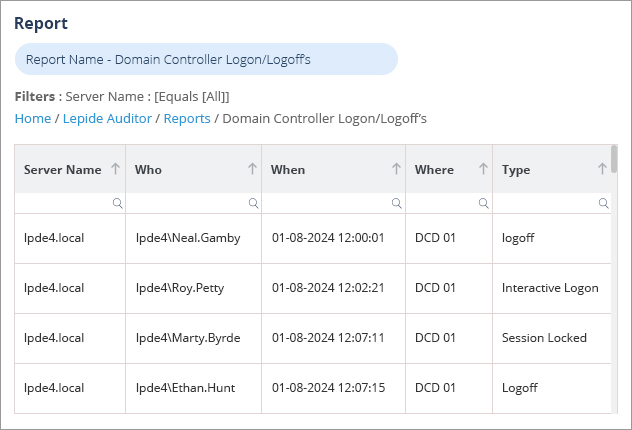
To run the Domain Controller Logon/Logoff’s Report:
- Select Lepide Auditor, Reports. From this screen, expand Active Directory and select Domain Controller Logon/Logoff’s
- Specify a date range
- Add a filter to show logon activity only
- Select Generate Report
- The report is generated and can be filtered, sorted and exported to CSV and PDF format

