It is crucial to keep track of changes to your Active Directory so that any potentially malicious activity can be quickly identified, and remedial action taken to ensure the security of your network.
The tracking of users’ logon events can help detect unusual logon patterns such as logons occurring at unusual times, logons to unauthorized hosts, and any other suspicious activities. It also helps administrators identify and respond to sudden spikes in failed logon attempts, as this could indicate the possibility of a brute force attack.
In this article, we will look at how to view Active Directory event logs using Event Viewer and then look at a more straightforward way to monitor logon events using the Lepide Auditor for Active Directory.
Using the Native Method
The Event Viewer is the native solution for reviewing security logs. It is free and is included in the administrative tools package of every Microsoft Windows system. After you enable Active Directory auditing, Windows Server writes events to the Security log on the domain controller. The security event log registers the following information:
- Action taken
- The user who performed the action
- The success of the event and any errors that occurred
- The time the event occurred
Events can be exported from the Event Viewer, however as different types of events have different schema, this complicates parsing the events to an audit file. Also, Event Viewer requires admins to learn the specific event ID numbers they want to search for or filter by, which makes the monitoring of changes to AD objects even more complex.
Another limitation of the native auditing solutions is that they do not provide the complete visibility which is required. The data is hard to read due to the lack of formatting and the searching of the event log is slow. Even using the default log size, you will have to spend a lot of time waiting for the search to finish, which will delay any threat response.
Enable Account Logon Events Auditing using the GPMC
Before you can use the Event Viewer, your domain’s audit policy needs to be enabled. The steps to do this are as follows:
- Open the Group Policy Management Console (GPMC) or run the command gpmc.msc:
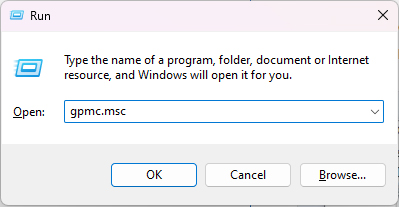
- Navigate to Domain Controllers and right click on the required domain controller’s policy and choose Edit
- In the Group Policy Management Editor, on the left pane, navigate to Computer Configuration, Policies, Windows Settings, Security Settings, Local Policies, Audit Policy
- Set the following audit policies:
- Audit account management: “Success”
- Audit directory service access: “Success”
- Audit logon events: “Success” and “Failure”
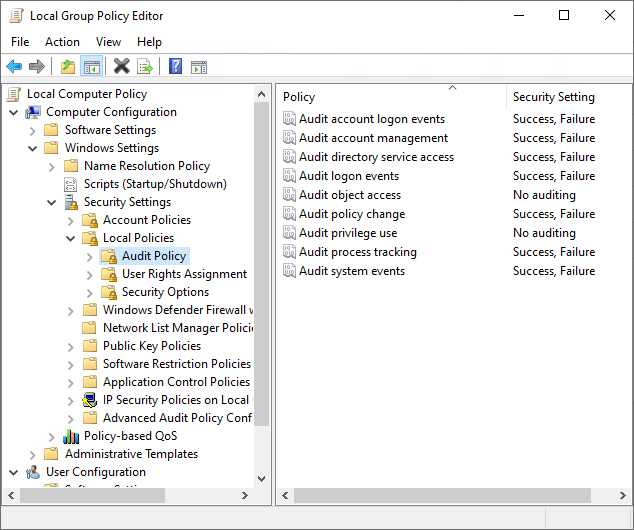
An alternative way to do this is to set Advanced audit policies:
- In the Group Policy Management Editor, expand Computer Configuration
- Go to Policies, Windows Settings, Security Settings, Advanced Audit Policy Configuration, Audit Policies and set the following audit policies:
Account Management
- Audit Computer Account Management: “Success”
- Audit Distribution Group Management: “Success”
- Audit Security Group Management: “Success”
- Audit User Account Management: “Success”
DS Access
- Audit Directory Service Access: “Success”
Logon/Logoff
- Audit Logoff: “Success”
- Audit Logon: “Success”
Find Account Logon Events Using the Event Viewer:
Once the above steps are complete, account logon events are recorded as event logs using various Event IDs. These events can be viewed in the Event Viewer by following the steps below:
- Click Start, Event Viewer
- On the left pane of the Event Viewer, navigate to Windows log, Security
- Here, you will find a list of all the security events that are logged
- On the right pane, under security, click on Filter current log
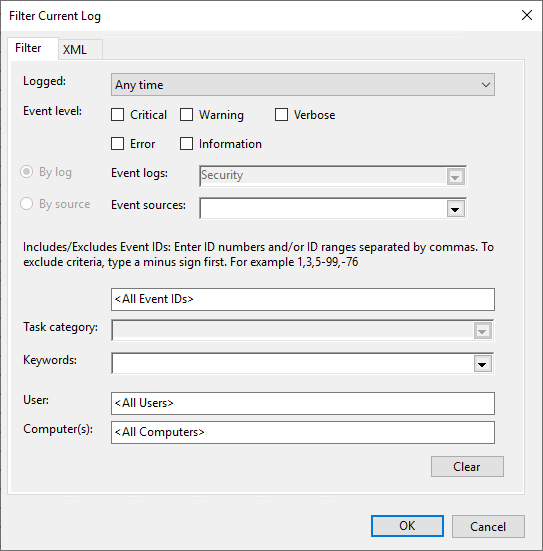
- In the pop-up window, enter the required Event ID and click OK
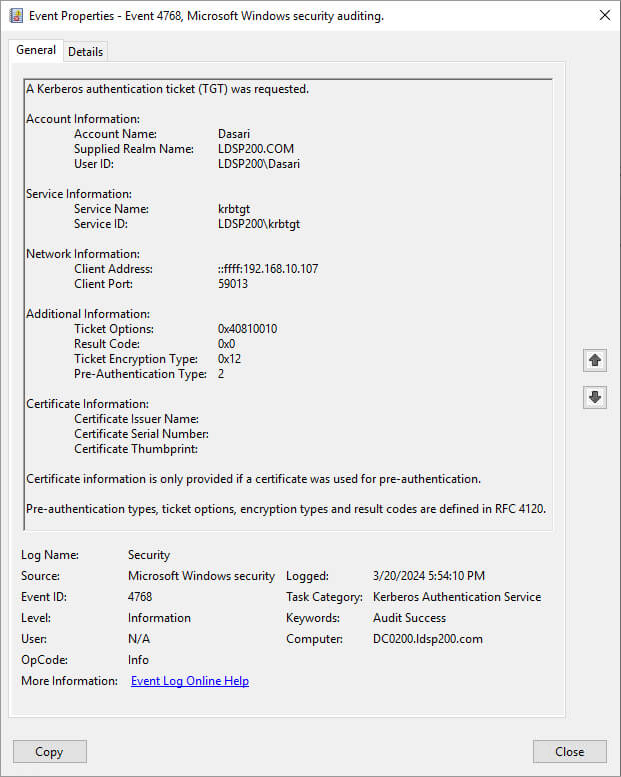
The example below shows the properties for Event ID 4768:
How Lepide can Help
As you can see, getting an overview of logon events on your network is a tedious task using native auditing. An administrator would have to search for the Event ID and view each event’s properties individually, which is highly impractical.
A more straightforward solution to this native way to track logon events is to use the Lepide Auditor for Active Directory. The Lepide Solution includes many pre-defined reports and alerts to monitor Active Directory activity and one example of these reports is the Domain Controller Logon/Logoff’s Report which is shown below:
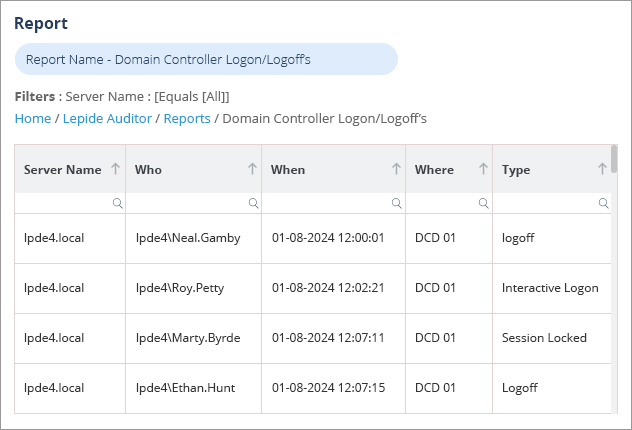
To run the Domain Controller Logon/Logoff’s Report:
- Select Lepide Auditor, Reports. From this screen, expand Active Directory and select Domain Controller Logon/Logoff’s
- Specify a date range
- Add a filter to show logon activity only
- Select Generate Report
- The report is generated and can be filtered, sorted and exported to CSV and PDF format

