As an administrator, you need to be always on the lookout for any activity that bucks the usual trends, as they could be indicative of an attack. Users with sufficient administrative rights can create any number of user accounts in Active Directory. These accounts can then be used to manipulate or steal sensitive data. It is therefore crucial to monitor and track account creations regularly to prevent malicious users from stealing sensitive data and conducting fraudulent acts. Let’s take a look at two ways to generate a list of user accounts created in Active Directory.
- By Using Native Method
- By Using Lepide Active Directory Auditor
Track Active Directory User Accounts Creation using Native Method
Please follow below given steps to enable auditing and audit relevant event logs:
Step1: Configuring the audit policy
- Type GPMC.MSC in the “Run” window to open “Group Policy Management” console. You can also access it from “Start Menu” or “Administrative Tools” in Control Panel.
- Go to “Forest” → “Domains” → “www.domain.com”→“Domain Controllers”.
- Edit any existingor newly create GPO at domain controller level to access “Group Policy Management Editor”. You can create a new GPO and link it to the domain.
NOTE: Our experts recommend never to edit the “Default Domain Policy” and “Default Domain Controller Policy”.
- Navigate to “Computer Configuration” → “Policies” → “Windows Settings” → “Security Settings” → “Local Policies”.
- Select “Audit Policy” to view its policies in the right pane
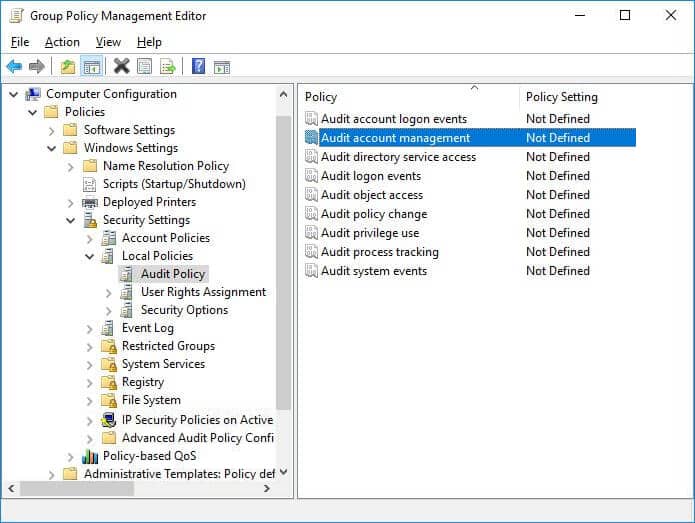
Figure 1: “Group Policy Management Editor” - Right-click “Audit account management”to access its properties.
- Click to select “Define these policy settings” checkbox. Select both “Success” and “Failure” checkboxes.
- Click “Apply” and “OK” to close “Audit account management Properties” window.
- Close “Group Policy Management Editor” window.
- In “Group Policy Management Console”, perform the following steps to apply this modified GPO to all Active Directory objects.
- Select the modified GPO.
- In the right pane’s “Security Filtering” section, click “Add” and type “Everyone” in the window that opens the screen.
- Click “Check Names” to validate the value.
- Click “OK” to add it.
- Close “Group Policy Management Console”.
- To update the applied policies, run the following command in “Command Prompt”:
gpupdate /force
Step 2: Tracking newly created accounts using Event Viewer
The event ID for user creation is 4720. Following is a screenshot of the same.
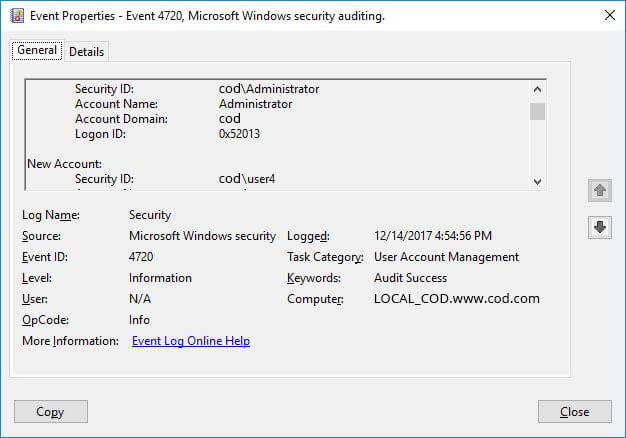
The steps to spot users created in the last 24-hours in the ‘Event Viewer” are:
- Open “Windows Event Viewer”.
- In the console tree, go to “Windows Logs” → “Security”.
- Click “Filter Current Log”,on the “Action” menu in the right-pane. In case if a filter is already applied, click “Clear Filter”.
- From “Logged” drop-down list, select the corresponding time period to filter the events based on when they occurred (here we select 24 hours from the list).
- Type Event ID (4720 for user account creation) in “Event IDs” that you want the filter to display.
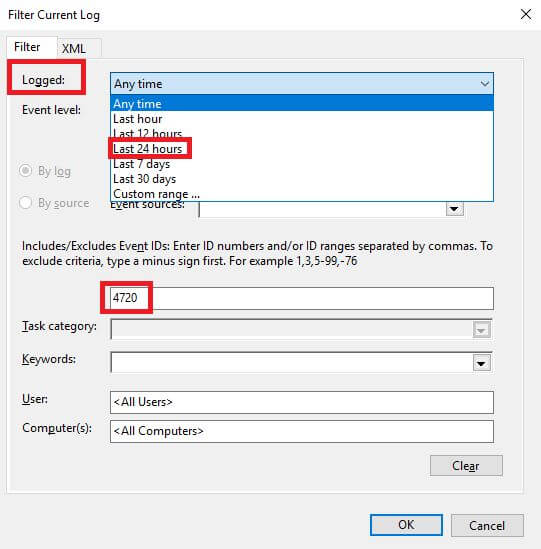
Figure 3: “Filter Current Log” window - To apply the filter, click “OK”
The screenshot given below displays a list of user accounts created in the last 24 hours:
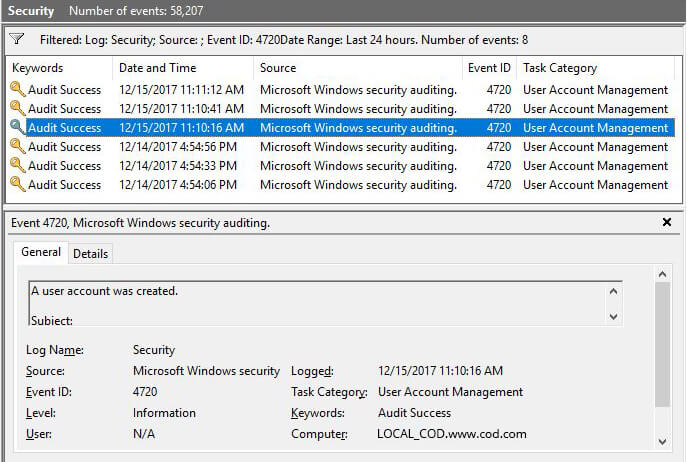
Figure 4: Users created in last 24 hours displayed in Event Viewer
Issues with Native Method
Native auditing is not without its faults. Admins have to collect and organize data from multiple event logs into a readable format to actually be able to detect any changes that appear irregular. The laborious nature of this task makes it difficult to identify potential threats before they manifest.
How to Use Lepide Active Directory Auditor to Get List of Accounts Created
Lepide Active Directory Auditor (part of Lepide Data Security Platform) helps IT admins keep an eye on activities in your Active Directory through real-time alerting and comprehensive reporting. Our solution enables you to perform attribute level filtering and sorting to get in-depth details for each of the reported events.
Following is a screenshot of a report generated using Lepide Active Directory Auditor showing details like who created a user, when it was created and from where:
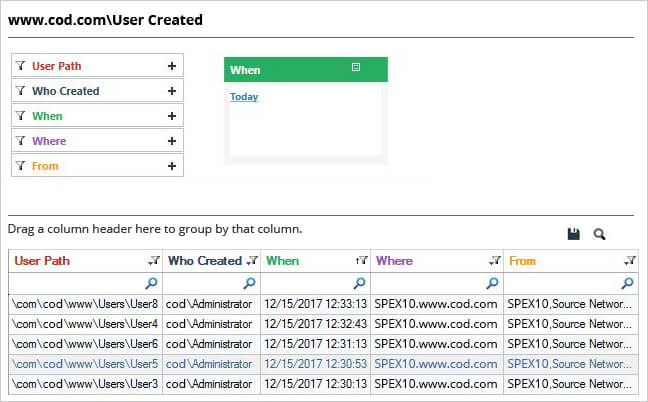
Our robust solution enables attribute level filtering and sorting options which offers in-depth details of each of the reported events.

