Cloud-based working offers many advantages including collaboration, flexibility, and reduced costs, but it also comes with potentially serious security threats. It is essential, therefore, to have proper controls in place to protect the privacy and integrity of the data you store in the cloud for your own security and to comply with regulatory controls.
To ensure continuous security and compliance with Microsoft 365, you need the same level of control as you do over your on-premises systems. Tracking Microsoft 365 login activity is therefore crucial to reduce risk and mitigate damage.
The native Azure (AD) audit logs record all logon events, but the entries are not easy to filter leaving you with a large volume of information to process manually.
In addition to the monitoring of Office 365 login history, it will also be necessary to store and access your Microsoft 365 login audit trail for several years. Using the native reports, you can only track activity for short periods of time meaning that if you don’t want to lose visibility into login activity, you have to constantly export data and store it.
A more straightforward solution to this native approach is to use the Lepide Auditor for Office 365. This Solution enables you to generate reports of both successful and failed attempts to login to Azure AD. Trusted locations can be filtered out to display only the information you are looking for, providing an efficient way to monitor Azure AD logons. And log files can be kept indefinitely meaning that you do not have to keep exporting and storing your data.
Here are two ways to detect logons in Azure AD and they are described below.
- Using the Microsoft 365 Admin Center
- Using the Lepide Auditor for Office 365
Check Login History Using Microsoft 365 Admin Center
To View Sign-ins:
- Log in to the Microsoft 365 Control Panel
- From the left-hand side menu, select Microsoft 365 Admin Center
- Then select Azure Active Directory under Admin Centers (select Show All if you can’t see the Admin Centers section)
- Select Users, All Users
- Select the User(s) you want to view sign-ins for
- Select Sign-in logs from the menu
- The results are displayed. The results can be filtered by using the Add filters option
Note: The login history information may take up to 24 hours to appear in the activity log.
Check Login History Using the Lepide Auditor for Office 365
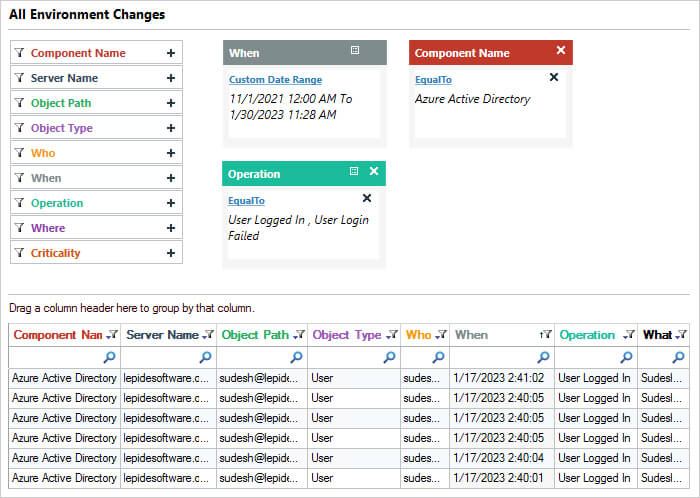
An alternative method to check login history in Office 365 is to use the All Environment Changes Report from the Lepide Auditor for Office 365. Our solution can detect logons outside of trusted locations in Azure AD.
- This report is listing all login activity for Azure Active Directory for a specified time period
- The report can be sorted, filtered, saved, and exported

