The auditing of NetApp file server logs allows you to identify suspicious or unauthorized activities, such as unauthorized access attempts, modifications, or deletions of files. This information is crucial for detecting security breaches, investigating incidents, and preventing future unauthorized access.
How to Check the Logs using Native Methods
Login to your cluster system and execute the following command:
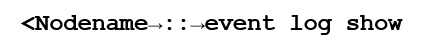
By default, the command displays EMERGENCY, ALERT and ERROR severity level events with the following information. The most recent events are listed first:
- The time at which the event occurred.
- The node in which the event occurred.
- The severity of the event.
- The event’s message.
To display detailed information about the events, use one or more of the optional parameters that affect how the command output is displayed and the amount of detail that is included. For example, to display all the details of the event, use the -detail parameter.
To display NOTICE, INFORMATIONAL or DEBUG severity level events, use the -severity parameter.
How Lepide can Help
A simpler, more straightforward approach to check NetApp Cluster Mode logs is to run the All File Server Interactions Report from the Lepide Auditor for NetApp Filer. An example of this report is shown below:
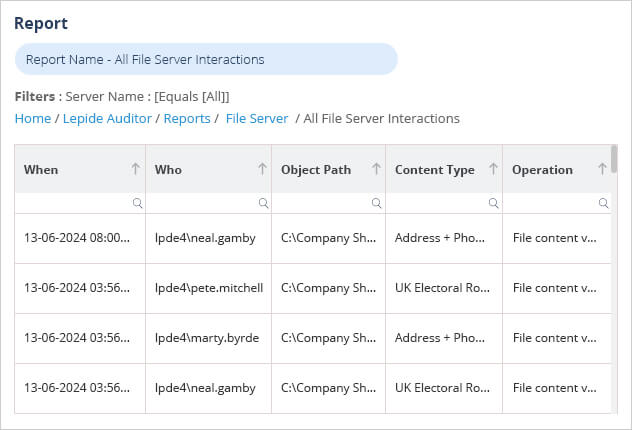
This report is run as follows:
- Select Lepide Auditor, Reports
- Select All File Server Interactions from File Server reports
- Specify a Date Range
- Select Generate Report
The report is generated and can be filtered, sorted and exported to CSV and PDF format.

