Microsoft Entra ID, formerly known as Azure Active Directory (Azure AD), is a cloud-based identity and access management service that employees can use to access external resources. These resources include Microsoft 365, the Azure portal, and many other SaaS applications.
By the continuous monitoring of network traffic and analysis of user behavior, Entra ID identifies any suspicious activities, detects unauthorized applications and stops unauthorized access attempts, ensuring that only trusted and secure applications operate on the system.
User demand has meant that there are now many enterprise application libraries available, however lack of understanding and management means that often unwanted applications are added, and employees download their own software, avoiding IT altogether.
This poses a risk to both security and compliance as by default Azure allows any user to give any application from the app gallery permission to access their data. This can be a problem as it provides an easy way for third-party apps to read any critical or sensitive content. Therefore, it’s crucial to continually monitor your Azure logs for any suspicious applications.
However, this can be a difficult task using manual tools. The Azure Audit log stores data on a directory-by-directory basis, so to search for data across different Azure directories, you need to run the same search multiple times. In addition, the native event log filters don’t contain an exclude function, so to filter out whitelisted applications, you will need to export the log data into a CSV file and analyze it from there.
In this guide we will look at two ways to detect illicit applications in Entra ID. The first is the native method using the Azure AD portal and the other is using the Lepide solution.
Using the Azure AD Portal
Please follow below steps:
- From the Azure Portal choose Monitor
- Select Audit Logs
- From the Category column select Application Management to filter the report. It will now show only application-related events. The Target(s) column will display the application name
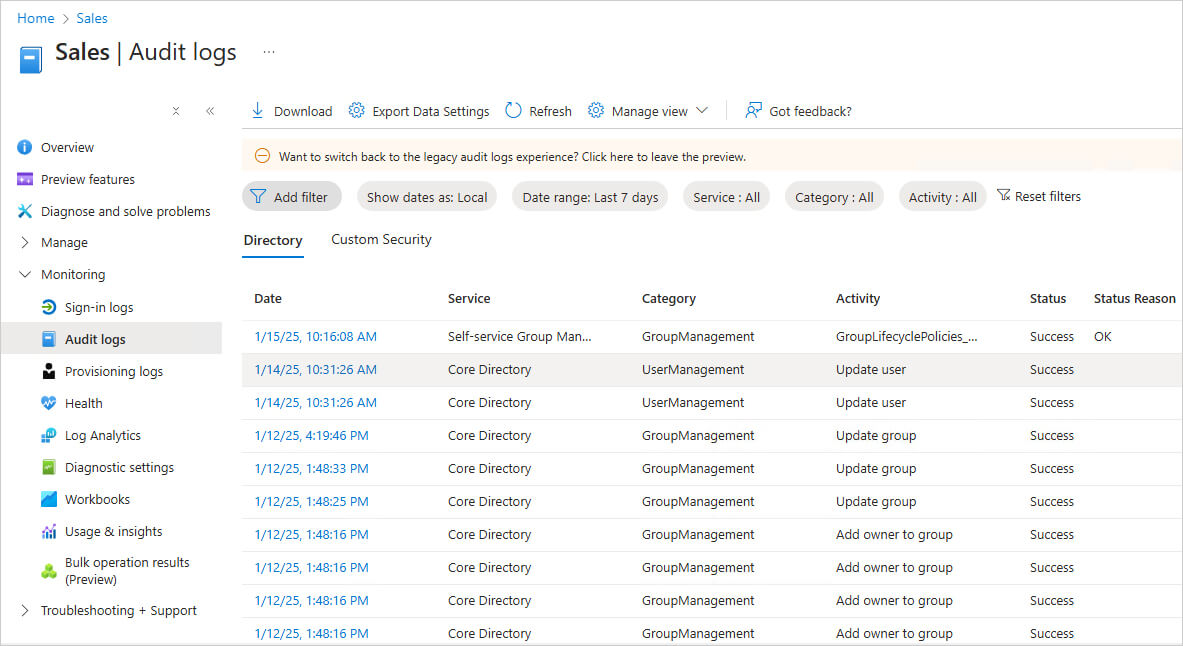
- The Details tab at the bottom of the page shows event details.
How Lepide Helps
The Lepide solution for Entra ID auditing allows you to report across all your audit data at once. You can choose which audit logs you want to see to prioritize the most important data to focus on. Alerts can be set up to notify you about suspicious activity to mitigate risk and prevent a data breach. In addition, the Lepide Auditor enables you to store your log files for compliance and investigation purposes.
To see all changes which have occurred in Azure AD, you can run the ‘All Azure AD Changes’ Report. An example of this is shown below:
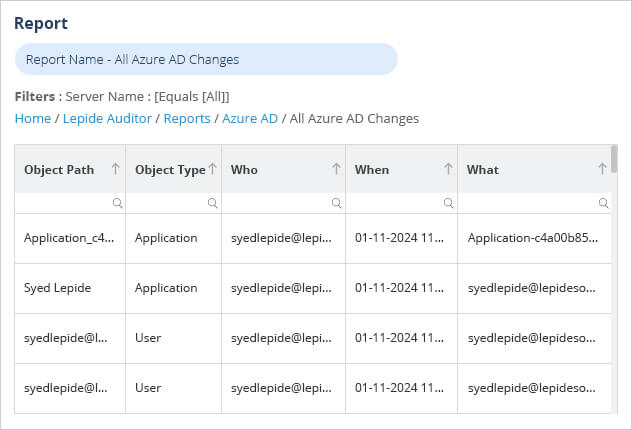
To run this report:
- Select Lepide Auditor, Reports
- From here, expand Azure AD
- Select All Azure AD Changes
- Specify a time frame if required
- Select Generate Report
The report is generated and can be filtered, sorted and exported to CSV and PDF formats.

