Weak passwords present a significant security risk for Active Directory and as most organizations are aware of this, they take action to protect user credentials.
However, if an attacker finds out the credentials for just one single user account in your network, it gives them a considerable amount of power. After logging on as a legitimate user, they can move across to other systems and escalate their privileges to deploy ransomware, steal critical data, disrupt vital operations and more.
A password policy established in Active Directory enforces password length, complexity, and history requirements, and can lock out an account after a certain number of failed login attempts.
But even with these controls in place, many people choose passwords that comply with company standards but are easy for them to remember, making them weak passwords. These weak passwords leave the organization vulnerable to one of the simplest methods that attackers use to gain access to a network which is to guess.
This strategy of guessing can be very effective. One example of a password guessing attack is a password spraying attack.
Password Spraying Attacks
In a password spraying attack, the attacker selects a commonly used password and uses it to try to log on to each account in an organization. Most of these attempts will fail, but a single failed logon for an account will not trigger an account lockout. If all the attempts fail, then further attempts can be made with the next password in their list. If they find a password that has been chosen by just one user in an organization, they can get inside your network and do significant damage.
In this article, we’ll show you how to audit Active Directory user passwords and find weak and simple passwords using PowerShell.
Install DSInternals PowerShell Module
The first method we can use to find weak passwords is the DSInternals (Directory Services Internals) third party PowerShell module. This will allow us to compare hashes of user passwords stored in the Active Directory database (ntds.dit file) with a dictionary of simple and common passwords.
This module contains several cmdlets that allow different actions to be performed with the Active Directory database in online or offline mode. In particular, the Test-PasswordQuality cmdlet allows for many different checks to be carried out at once. This function checks for weak passwords via a predefined list, duplicate passwords, default passwords set via the administrator but not changed, passwords which never expire and empty passwords.
As would be expected, user passwords cannot be obtained from the AD database as plain text. Passwords stored in Active Directory are hashed, but you can compare the password hashes of AD users with the hashes of words from a dictionary file and highlight any weak passwords.
In PowerShell version 5 (and newer), you can install the DSInternals module online from the official PowerShell script gallery as follows:
Install-Module DSInternals
Use Test-PasswordQuality Cmdlet to Find Week Passwords
Next, you need to create a password dictionary. It will be a simple text file with a list of commonly used, weak, and other bad passwords. You can download a password dictionary file from the Internet or create one yourself. The DSInternal module allows you to compare the hashes of your users’ passwords in Active Directory with the hashes of words from this file. Save the passwords to a text file PasswordDict.txt.
The next step is to create a small PowerShell script. In the following variables, specify the path to the password file, the domain name, and the domain controller name:
Install-Module DSInternals
$DictFile = "C:\Users\lashika\Desktop\lashika\Lashika\PasswordDict.txt"
$domain = "dc=ldsp2,dc=com"
$dc = "192.168.30.180"
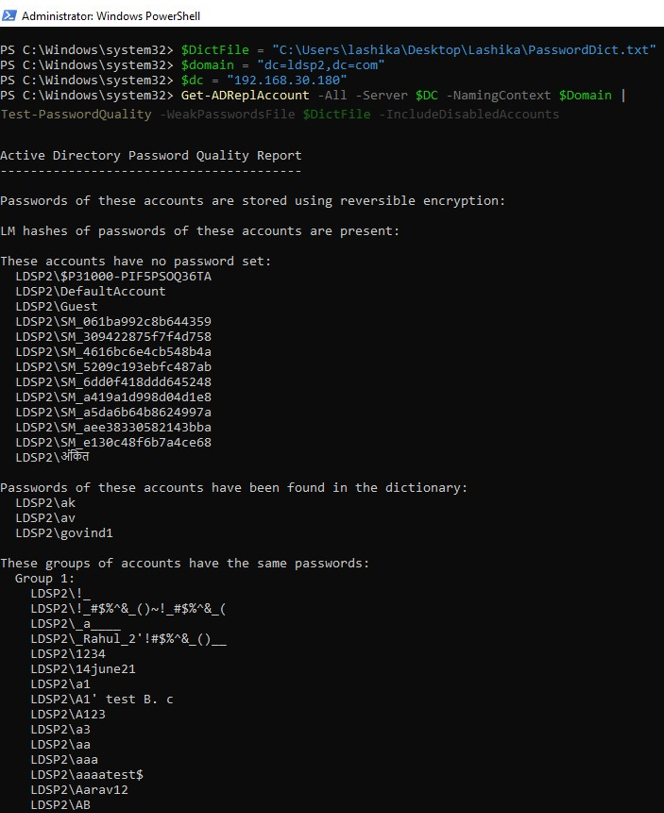
Then using the Get-ADReplAccount cmdlet, get a list of users in AD (like Get-ADUser). Additionally, this cmdlet returns their NT and LM hashes, as well as the hash history. Then, for each user, compare the hash of the password with the hashes from the dictionary file (the check is also performed for disabled user accounts):
Get-ADReplAccount -All -Server $DC -NamingContext $Domain | Test-PasswordQuality -WeakPasswordsFile $DictFile -IncludeDisabledAccounts
The result of running the script may look like this:
How Lepide Helps with Active Directory Security
The Lepide Data Security Platform offers an Active Directory security solution which will proactively monitor, detect issues, and optimize performance of your AD for a reliable directory infrastructure. The Lepide Solution enables you to do the following:
- It gives you complete visibility into passwords that never expire. The Lepide Solution can notify users about their password expiry date and remind them to reset their passwords. Follow-up notifications are also available for users who fail to take immediate action.
- Identify and address security weaknesses and risk in your Active Directory by detecting inactive users (often a target for ransomware), users with passwords that never expire (non-compliant), group membership changes (causing privilege escalation), and more.
- Monitor Active Directory for signs of compromise using our monitoring tool which comes with out-of-the-box threat models to detect a wide variety of potential threats to your AD security, including brute force attacks, password compromise, permissions escalation and more.
- Manage permissions with Active Directory monitoring using an advanced monitoring tool that enables you to get a better understanding of the structure of your AD, and the way in which users are deriving their permissions.
- Monitor Active Directory health and performance to provide a simple and powerful means of monitoring important elements of your Active Directory ensuring continuity and health of the environment.

