Accounts with privileged credentials give potential attackers the permissions they need to get inside critical systems. To reduce this risk, it is essential to remove unnecessary permissions by following the Principle of Least Privilege (PoLP).
The Principle of Least Privilege is the practice of limiting user profile privileges to the bare minimum of what is necessary for the user’s specific job requirements. When done correctly, following the PoLP can successfully reduce the risk of privilege abuse and insider threats by limiting the potential attack surface.
To implement this approach, you can either use Active Directory Users and Computers (ADUC) to manually review user object properties or use PowerShell scripts to generate reports that list specific domain local group names (such as Enterprise Admins and Domain Administrators) and then manually check which groups a particular user account belongs to.
However, both of these options are time consuming and can be complex; and if you want to filter your report or add more details, you will need more expertise in PowerShell scripting and cmdlet parameters.
In this article, we will look at two native methods, ADUC and PowerShell, for finding Active Directory User’s Group Membership. We will then look at a more straightforward solution using the Lepide Auditor.
1. Using Get-ADPrincipalGroupMembership Cmdlet
Please below given steps
- Open the PowerShell ISE
You will need to download the correct Remote Server Administration Tools (RSAT) package for your OS if you don’t have the Active Directory module installed on your Windows machine
To activate the module, use the import-module ActiveDirectory command from an elevated PowerShell prompt
- Run one of the following PowerShell scripts, specifying the AD user account name (samaccountname) you’re querying and the path to export to
This report will output the user group list with group categories and scope:
Import-Module ActiveDirectory
$UserName = “T.Simpson[SO1]“ | Get- groupcategory, groupscope | ADPrincipalGroupMembership $Usernameor
Add-ADPrincipalGroupMembership -Identity Admin -MemberOf DC_Admin
1. Using Parameters with the Get-ADPrincipalGroupMembership
The following parameters can be used with the Get-ADPrincipalGroupMembership cmdlet:
- AuthType
- Credential
- Identity
- Partition
- ResourceContextPartition
- ResourceContextServer
- Server
Get-ADPrincipalGroupMembership Cmdlet Examples
The following examples illustrate the use of the Get-ADPrincipalGroupMembership cmdlet:
- Get the Group Memberships for the Domain Administrator
To view the group membership of the built-in administrator of a domain, use the following cmdlet:
Get-ADPrincipalGroupMembership administrator
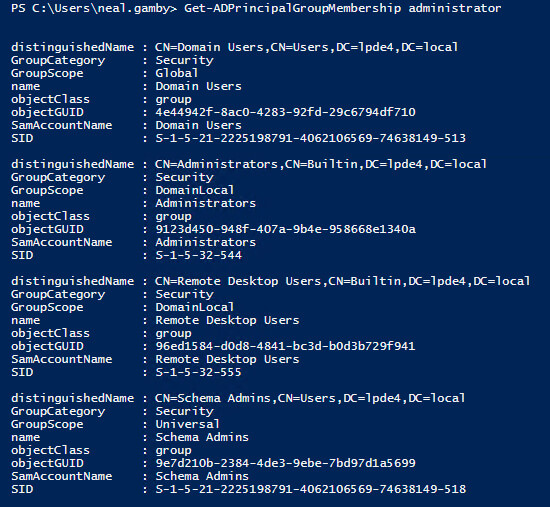
By default, the built-in administrator is a member of commonly known security groups such as Administrators, Backup Operators, Schema Admins, Enterprise Admins and Domain Admins.
- View Group Membership Information in Tabular Form
- Filter Groups using Get-ADPrincipalGroupMembership
If you prefer to view this information in a tabular form, use the command below.
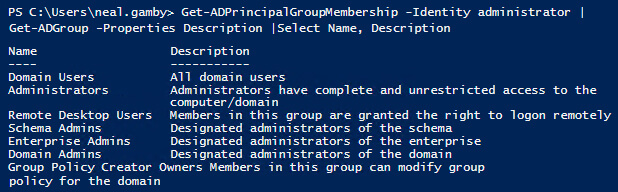
The first step is the Get-ADPrincipalGroupMembership gets the group memberships of the user specified in the Identity parameter. That result is passed to Get-ADGroup, which gets the details about the groups. That information is passed to the third cmdlet, Select, which prints the name and description of each group that the user is a member of.
Get-ADPrincipalGroupMembership -Identity administrator | Get-ADGroup -Properties Description | Select Name, Description
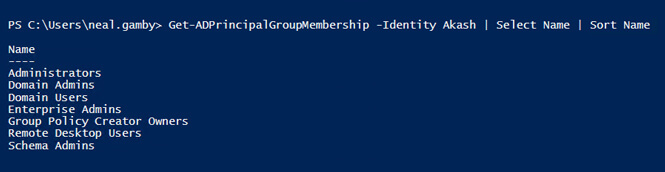
To filter the groups that the user is a member of, run the following command:
Get-ADPrincipalGroupMembership -Identity Akash | Select Name | Sort Name
2. Using the Whoami Cmdlet
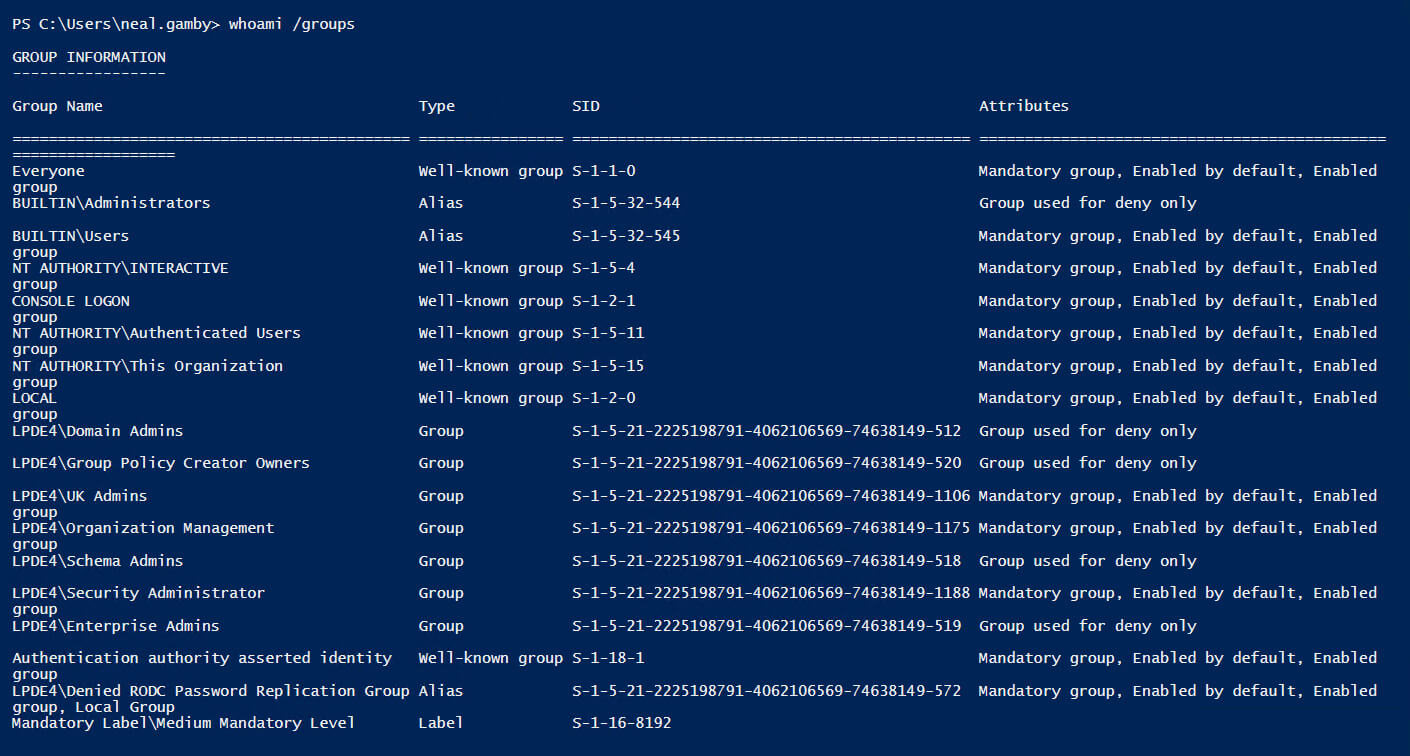
An alternative option is for a logged-on user to use the following command to see their group memberships:
Whoami /groups
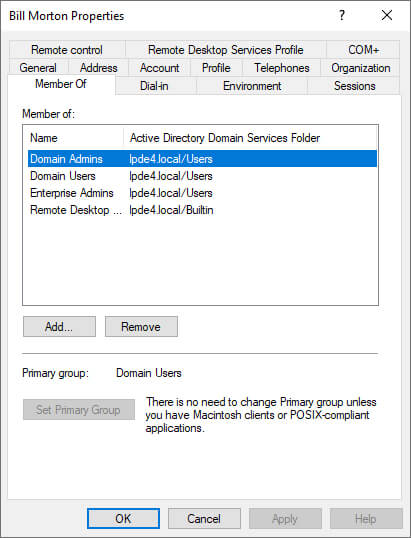
2. Using Active Directory Users and Computers (ADUC)
ADUC remains the most common way to investigate a user’s group memberships. Simply launch the console, open the user’s properties, and go to the MemberOf tab, as shown below:
How Lepide Helps
An alternative, more straightforward, solution to this native method, which requires no knowledge of PowerShell, is to use the User’s Group Membership Report included as part of the Lepide Active Directory Auditor. This report lists all users alongside the groups to which they belong. This report can be exported to CSV, PDF or MHT format:
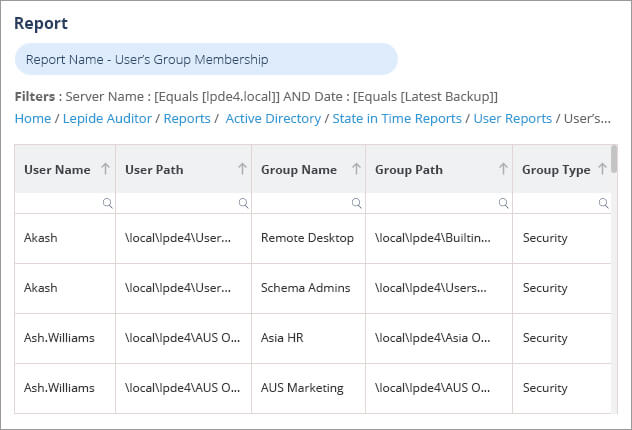
Please follow below steps to run the report:
- Click the ‘User & Entity Behavior Analytics’ icon and select Active Directory Reports, Active Directory State Reports, User’s Group Membership
- Click Generate Report
- The report will run and can be sorted, filtered, grouped, saved, and exported

