Having an understanding of what your users are doing in your critical systems is a crucial part of identifying potential suspicious behavior leading to security breaches. Tracking user activity provides the necessary information to spot malicious activity and stop an organization from falling prey to a potential cyberattack.
Native Active Directory auditing tools can be used to monitor user activity, but it is a time-consuming and often complex task. Lepide Auditor overcomes the limitations of native auditing by giving you the visibility you need to detect and react to insider threats quickly and efficiently.
In this article, we will look at two methods for tracking user activity: the native auditing method (Event Log) and an automated solution using Lepide Auditor.
Track User Activity in Windows Computers using Event Logs
Please follow below steps:
- Enable Audit Policy
- Select Server Manager on Windows server.
- Under the Manage tab, open the Group Policy Management console.
- Go to Forest, Domain, Your Domain, Domain Controllers.
- You can either edit an existing group policy object or create a new one.
- In the Group Policy Editor, navigate to Computer Configuration, Policies, Windows Settings, Security Settings, Local Policies, Audit Policy.
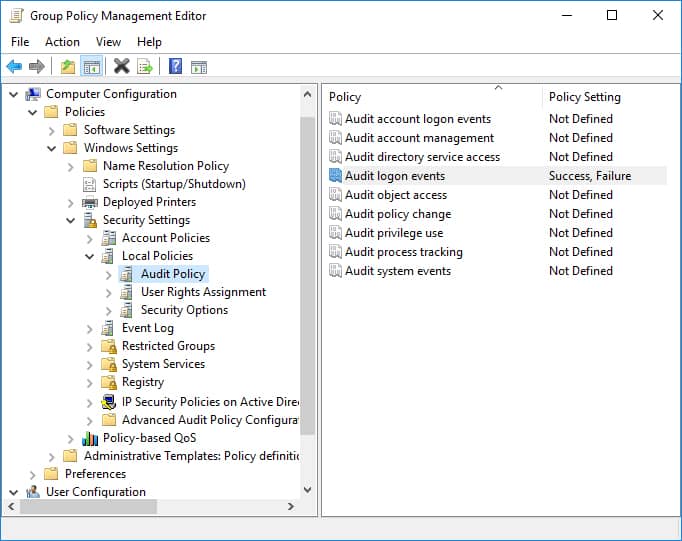
- In Audit Policy, select Audit logon events and enable Success and Failure auditing.
- Enable logon-logoff
- Go back to Computer Configuration. Navigate to Windows Settings, Security Settings, Advanced Audit Policy Configuration, Audit Policy, Logon/Logoff
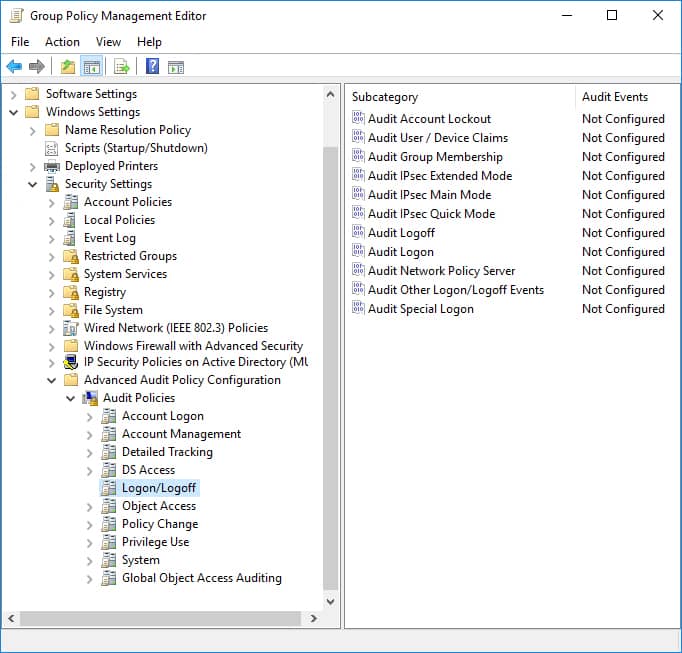
- Next, enable Success and Failure auditing for Audit Logon, Audit Logoff, and Audit Special Logon.
- Open the Group Policy Management console and select the GPO that you have edited or created.
Under Security Filtering, add the users whose logons need to be tracked. You can also choose to audit every domain user’s logon by selecting All users. To audit, a group of domain users, the specific group(s) can be added.
- Go back to Computer Configuration. Navigate to Windows Settings, Security Settings, Advanced Audit Policy Configuration, Audit Policy, Logon/Logoff
- Use Active Directory Event Viewer to check the logs
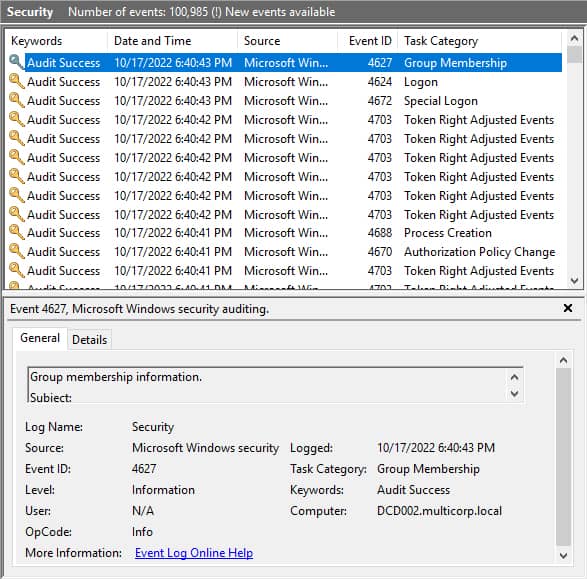
- Open Event Viewer and navigate to Windows logs, Security.
- Look for the event IDs:
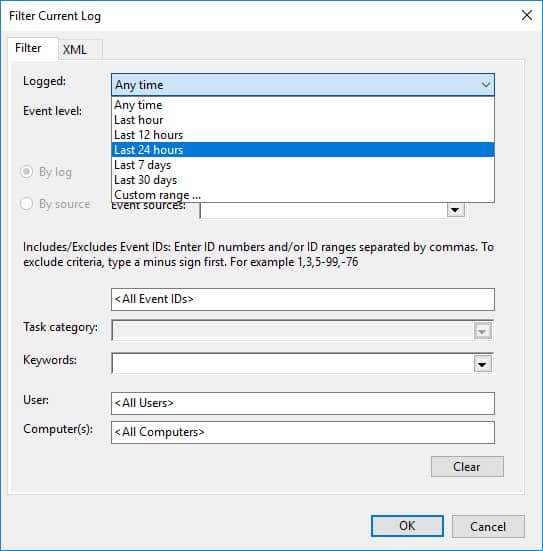
- Click Filter Current Log on the right side to filter the logs based on event IDs or the time range for which the information is required.
- System admins have to go through the list of logon times and identify suspicious patterns if any. This is a tedious and error-prone process as there is a high chance that some logs may be overlooked.
Monitor User Activity in Windows Computers Using the Lepide Auditor
Lepide Auditor for Active Directory overcomes the complexity of the native method by providing a straightforward way to identify suspicious insider activity using Active Directory by using Logon/Logoff Reporting and the Permissions Modification Report.
Lepide Auditor for Active Directory includes several Logon/Logoff reports to track logon activity. Two of these reports are Failed User Logon and Successful User Logon/Logoff Reports.
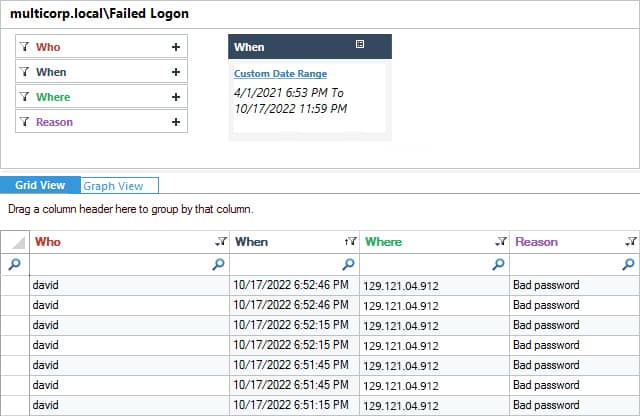
How to run the Failed Logon Report:
- Click the User & Entity Behavior Analytics icon and select Active Directory Reports, Logon/Logoff Reports, Failed Logon
- Select a Date Range and click Generate Report
- The report is generated and can be sorted, filtered, grouped, saved, and exported.
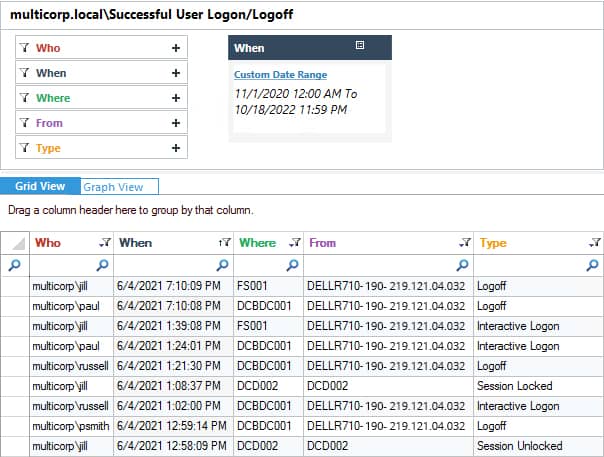
How to run the Successful User Logon/Logoff Report:
- Click the User & Entity Behavior Analytics icon and select Active Directory Reports, Logon/Logoff Reports, Successful User Logon/Logoff
- Select a Date Range and click Generate Report
- The report is generated and can be sorted, filtered, grouped, saved, and exported.

