In organizations comprising thousands or even hundreds of thousands of user accounts and computer objects, how can you be expected to effectively find and manage inactive user accounts in Active Directory?
Inactive users in Active Directory (AD) are accounts that have not been used for a certain period of time. The exact time frame for considering an account as inactive may vary depending on the organization’s policies and security requirements. In general, an account is considered inactive if the user has not logged in for a specified period of time, typically 30, 60, or 90 days. Inactive user accounts can be a security risk because they may still have access to resources or systems, and their credentials may be compromised without being noticed.
Active Directory user and computer accounts can become obsolete for many reasons; including long leaves or employees quitting an organization. Disabling and removing unused or stale user and computer accounts in your organization, helps to keep Active Directory safe and secure from insider attacks. This article explains the steps to handle inactive accounts by using native methods and by using Lepide’s Active Directory Cleanup tool.
Why is it Important to Find and Manage Inactive Users in AD?
Inactive users in Active Directory (AD) can present several security risks. Some of the major ones are:
- Unauthorized access: Inactive user accounts may still have access to certain resources, such as network drives or applications. If these accounts are not disabled or deleted, they can be used to gain unauthorized access to sensitive data.
- Password guessing attacks: Attackers can use inactive user accounts to launch password-guessing attacks. If the passwords for these accounts are weak or have not been changed for a long time, they may be easily guessed or cracked, which can lead to a security breach.
- Privilege escalation: Inactive user accounts that have administrative privileges can be used to escalate privileges and gain access to more sensitive systems and data.
- Malware propagation: Inactive user accounts can be used as a vector for malware propagation. Attackers can compromise an inactive account and use it to spread malware throughout the network.
- Compliance violations: Inactive user accounts can violate compliance requirements, such as the General Data Protection Regulation (GDPR), the Payment Card Industry Data Security Standard (PCI DSS), and others. These regulations require organizations to maintain control over user accounts and ensure that only authorized personnel have access to sensitive data.
For the above reasons, it’s vital that you are able to proactively find and effectively manage inactive Active Directory user accounts.
Manage Inactive User and Computer Accounts using Native Method
The period after which unused user and computer accounts become inactive varies from organization to organization, but it is usually around 15 to 30 days.
Follow the below steps within the specific time intervals in your organization will help you deal with these obsolete accounts.
Step 1: List Inactive Accounts
Execute the following commands to search the dormant accounts in the Active Directory.
-
- Run the command given below in the “Command Prompt” to get a list of inactive user accounts:
dsquery user -inactive 15-
- Run the command given below in the “Command Prompt” to get a list of inactive computer accounts:
dsquery computer -inactive 15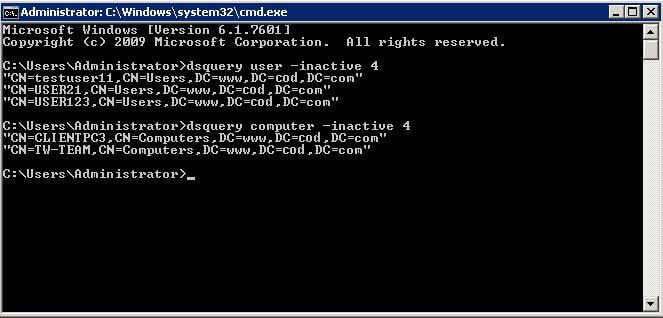
Step 2: Manage Inactive Accounts
After listing inactive accounts, you manage them by performing the below given methods (you can choose any method from these):
- Reset passwords of inactive accounts
- Disable the Inactive Accounts
- Move the account to an Organizational unit
- Delete the inactive accounts
Perform the following steps just after listing the inactive accounts.
- Navigate to “Start” → “Administrative Tools” → “Active Directory Users and Computers”.
- Right-click the inactive user and click “Reset Password”
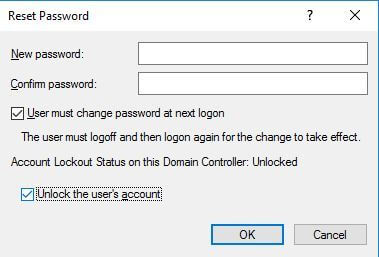
Figure 2: Resetting account password - Enter new passwords.
- Click “OK”.
Method 2 – Disable the Inactive Accounts
The inactive accounts must be disabled within 15-60 days to prevent any further security threats, using the commands given below:
-
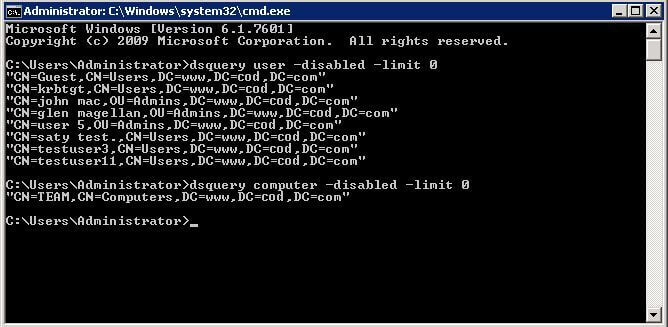
- To disable the user accounts, run the following command in “Command Prompt”.
dsquery user -disabled -limit 30-
- For disabling inactive computer accounts, run the following command in “Command Prompt”.
dsquery computer -disabled -limit 30NOTE: Here, 30 days is the inactivity period and you can change it.
Method 3 – Move the account to an Organizational unit
After a few days of disabling the accounts, these should be moved to a stand-alone organizational unit. Right-click the username, select “Move” from the context menu and move the user to a standalone Organizational Unit. You can also drag-and-drop the user and computer account to any Organizational Unit.
Method 4 – Delete the inactive accounts
All the disabled inactive accounts after being moved to an organizational unit must be deleted to make sure that no one can use them at all. Execute the following commands.
-
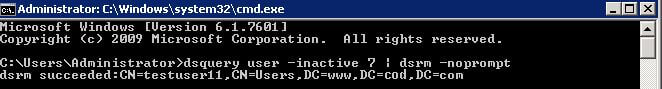
- Run the command given below to delete the disabled user accounts
dsquery user -inactive 50 | dsrm–noprompt-
- Run the command given below to delete disabled computer accounts:
dsquery computer -inactive 7 | dsrm –nopromptNOTE: Here, 50 days is the inactivity period and you can change it.
Issues with the Native Method
All these steps have to be performed manually, which consumes a lot of time and effort. Also in the absence of an automated system, the steps mentioned above are not performed automatically at scheduled intervals, creating more manual work for IT teams.
This task becomes even more complicated when dealing with hundreds of accounts, as users will need an in-depth understanding of PowerShell cmdlets to extract the required information.
How to Use Lepide Active Directory Cleaner to Find and Manage Inactive Accounts
Lepide Active Directory Cleaner is a simple and cost-effective solution, which enables you to detect and manage inactive accounts in Active Directory. It is an integral part of Lepide Data Security Platform solution. Our solution helps you get a complete list of all the obsolete accounts prevalent in your environment.
Following is a screenshot of Active Directory Cleaner settings.
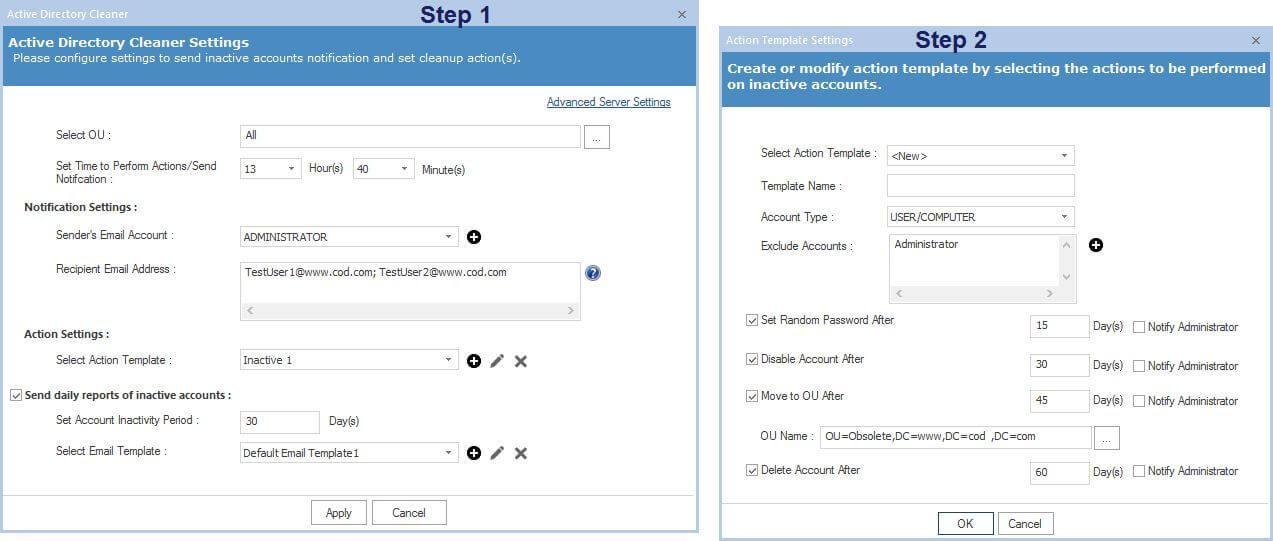
After a simple configuration, these actions can be performed automatically, helping you to increase the security of your Active Directory.

