In this article, I’ll show you how to create and manage Organizational Units using Windows PowerShell.
Organizational Units (OUs) are special containers in Active Directory (AD) that can be used to help you manage objects like computers and users. For example, you might create an OU to manage all SQL database servers or domain controllers. Using PowerShell, you can create, rename, move, and delete OUs. You can also use PowerShell to move AD objects between OUs and link Group Policy Objects to them.
Create an OU
Let’s start off by creating a new OU using New-ADOrganiaztionalUnit. You need to run the following commands on a device that has the Active Directory module for PowerShell installed and you must be logged in with an account that has permission to modify AD. The command below creates an OU called Finance, which is protected from accidental deletion, in the Departments OU located in the ad.contoso.com domain.
New-ADOrganizationalUnit Finance –Path 'OU=Departments,DC=ad,DC=contoso,DC=com' -ProtectedFromAccidentalDeletion $TrueBoth the -Path and -ProtectedFromAccidentalDeletion parameters are optional. If you don’t include a path, then the new OU will be created in the AD root. You can remove accidental deletion protection on an OU using Set-ADOrganizationalUnit:
Set-ADOrganizationalUnit -Identity 'OU=Departments,DC=ad,DC=contoso,DC=com' -ProtectedFromAccidentalDeletion $FalseMove an OU
Use the Move-ADObject cmdlet to move an OU as shown below. If the OU you want to move has its ‘Protected from accidental deletion’ flag set to ‘True’, before running the move command you’ll need to disable the flag using Set-ADOrganizationalUnit. The command moves the Finance OU from the Departments to the Sensitive OU.
Move-ADObject -Identity 'OU=Finance,OU=Departments,DC=ad,DC=contoso,DC=com' -TargetPath 'OU=Sensitive,DC=ad,DC=contoso,DC=com'Rename an OU
The following command renames the Finance OU to Accounts:
Rename-ADObject -Identity 'OU=Finance,OU=Sensitive,DC=ad,DC=contoso,DC=com' -NewName AccountsLink a Group Policy Object to an OU
Organizations commonly manage servers and end-user devices with Group Policy. You can link Group Policy Objects (GPOs) to OUs using the New-GPLink cmdlet. The command below links a GPO, called ‘Sensitive PCs’, to the Accounts OU. The -LinkEnabled and -Enforced parameters control whether the GPO will be processed on objects in the OU and whether it can be blocked by GPOs linked to a lower container or OU.
New-GPLink -Name ‘Sensitive PCs’ -Target 'OU=Accounts,OU=Sensitive,DC=ad,DC=contoso,DC=com' -LinkEnabled Yes -Enforced YesOptionally, the -Order parameter lets you specify a number between one and the number of GPO links on the target OU, site, or domain. The higher the number, the higher priority the GPO gets during processing. The code below lists any GPOs linked to the Accounts OU, starting with the GPO that has the lowest priority.
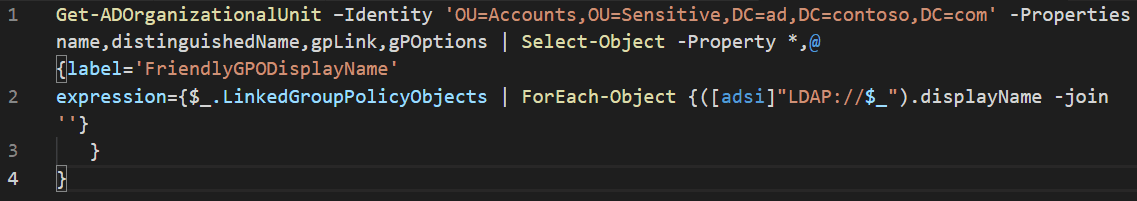
Get-ADOrganizationalUnit –Identity 'OU=Accounts,OU=Sensitive,DC=ad,DC=contoso,DC=com' -Properties name,distinguishedName,gpLink,gPOptions | Select-Object -Property *,@{label='FriendlyGPODisplayName'
expression={$_.LinkedGroupPolicyObjects | ForEach-Object {([adsi]"LDAP://$_").displayName -join ''}
}
}Move AD Objects to an OU
Again, using the Move-ADObject cmdlet, you can move computer and user objects to an OU. Note here that CN is used instead of OU in front of the username object and Users container name. The command moves David Smith’s user account from the Users container to the Accounts OU.
Move-ADObject -Identity 'CN=David Smith,CN=Users,DC=ad,DC=contoso,DC=com' -TargetPath 'OU=Accounts,OU=Sensitive,DC=ad,DC=contoso,DC=com'Delete an OU
Finally, let’s delete the Accounts OU using the Remove-ADOrganizationalUnit cmdlet.
Remove-ADOrganizationalUnit -Identity 'OU=Accounts,OU=Sensitive,DC=ad,DC=contoso,DC=com' -RecursiveThe -Recursive parameter removes all child objects regardless of whether they are protected from deletion. Unless the OU has no child objects, you must specify the -Recursive parameter.
Conclusion
An important part of managing OUs is being able to determine whenever any unwanted changes are made to the OUs themselves or the surrounding permissions. PowerShell is very limited when it comes to this kind of organizational unit change auditing. Lepide Active Directory Auditor (part of Lepide Data Security Platform) will enable you to track all modifications and permission changes to OUs, to ensure that nothing untoward is taking place in your critical Active Directory environment.

