Monitoring Active Directory group membership changes is crucial for maintaining a secure and well-managed IT environment. Group membership determines access privileges and permissions to sensitive resources and systems within an organization.
Here are the key reasons why monitoring these changes is important:
By monitoring group membership changes, organizations can detect and respond to unauthorized access attempts. Any unauthorized addition or removal of users from critical groups could signify a security breach or insider threat. Prompt detection allows for immediate investigation and mitigation, preventing potential data breaches or unauthorized system access.
In addition, many regulatory frameworks, such as the Payment Card Industry Data Security Standard (PCI DSS) or the General Data Protection Regulation (GDPR), require organizations to maintain strict access controls and regularly audit user permissions. Monitoring group membership changes helps ensure compliance with these regulations, reducing the risk of penalties or legal consequences.
Monitoring group membership changes also establishes accountability for any changes made. It allows administrators to identify who made the modifications, when they occurred, and the reasons behind them. This information is valuable for auditing purposes and assists in troubleshooting and tracking any inappropriate actions.
Finally, Active Directory group membership changes often result from employee onboarding, offboarding, or role changes. Monitoring these changes helps organizations maintain proper change management practices, ensuring that users have appropriate access privileges and that the principle of least privilege is enforced consistently.
In this article, we go through how to audit and track Active Directory group membership changes. We will go through the native method first, and then we will show how much simpler the process is when using Lepide Active Directory Auditor.
Track Active Directory Group Membership Changes using Event Logs
Below are the steps for native auditing
Step 1: Enable Active Directory Auditing through Group Policy
- Type GPMC.MSC in “Run” box and press “Enter.” The “Group Policy Management” console opens up.
- Go to “Forest” → “Domains” → “www.domain.com” in the left panel.
- Right-click the “Default Domain Policy” or any customized domain-wide policy. (However, we recommend you to create a new GPO, link it to the domain, and edit it).
- Select “Edit” to access “Group Policy Management Editor.”
- Next, navigate to “Computer Configuration” → “Policies” → “Windows Settings” → “Security Settings” → “Local Policies” → “Audit Policies”.
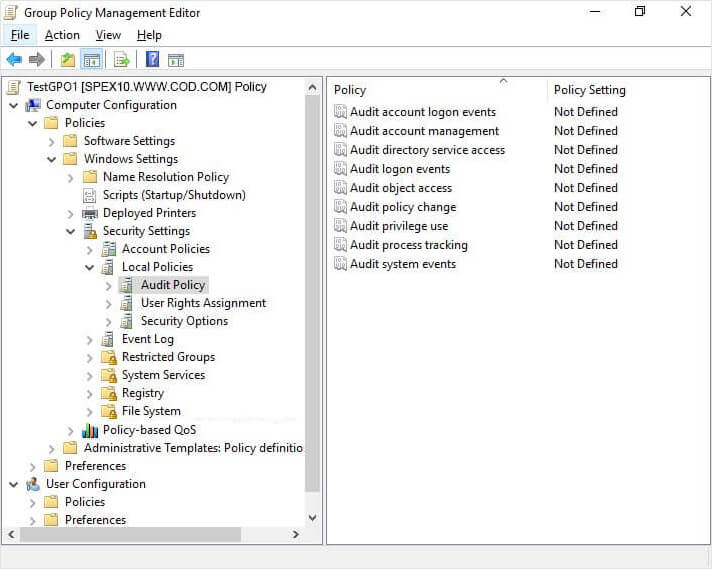
Figure 1: Group Policy Management Editor - Management and access properties.
- Click to select the “Define these policy settings” option.
- Select both the “Success” and “Failure” checkboxes to enable audit policy for monitoring successful events.
- Now, close “Group Policy Management Editor”.
- After closing it, you will be back at “Group Policy Management Console”. Select the GPO that you have modified.
- In the “Security” filtering section in the right pane, click “Add” to apply this GPO to all objects of Active Directory. Type “Everyone” in the dialog box that opens up. Click “Check Names” and “OK” to add the value.
- Close “Group Policy Management Console”.
- It is recommended to update the Group Policy instantly so that new changes can be applied to the entire domain. Run the following command at the Command Prompt or in the “Run” box to update the Group Policies on all domain controllers.
gpupdate /force
Step 2: Enable Auditing of Active Directory through ADSI edit
- In “Start Menu” or in “Control Panel”, “Administrative Tools” and open “ADSI Edit.”
- Right-click the ADSI Edit node in the left panel and select “Connect To”.
- In the “Connection Settings” window, select “Default Naming Context” in the drop-down menu of selecting a well-known Naming Context.
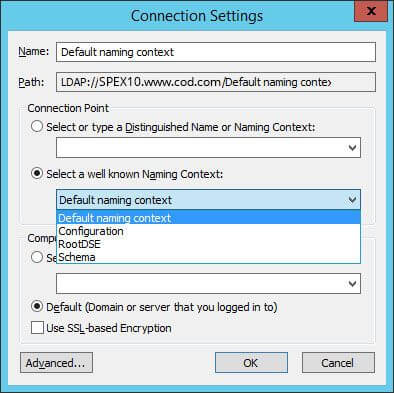
Figure 2: Connection Settings for ADSI Edit - Click “OK” to establish the connection to the Default Naming Context of the domain. It is a node displayed in the left tree pane, just below the top ADSI Edit node.
- Expand “Default Naming Context [dc.www.doamin.com]” and access the top node under it.
- Right-click this top node having the fully qualified domain name and click “Properties” in the context menu.
- In the properties, switch to the “Security” tab and click the “Advanced” button to access “Advanced Security Settings for www”.
- Switch to the “Auditing” tab and click the “Add” button to add a new auditing entry. It shows the “Auditing Entry for www” window on the screen.
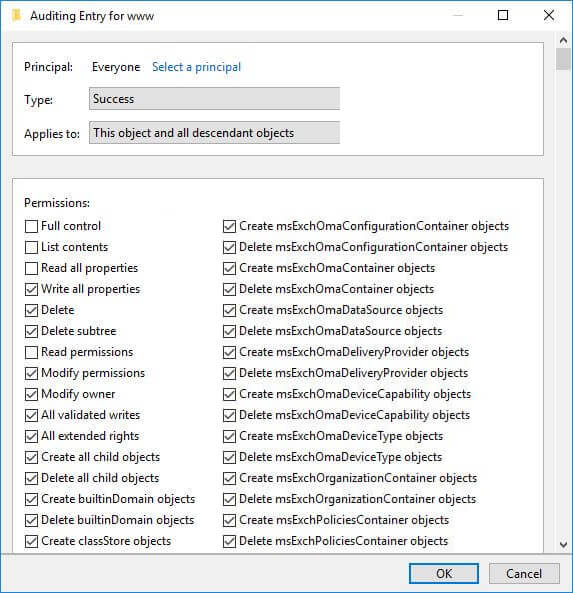
Figure 3: Auditing Entry window - Click “Select a principal” to add“Everyone”.
- Select type as “Success” and applies to as “This object and descendant objects.”
- Under “Permissions,” select all checkboxes by clicking “Full Control,” except the following permissions.
- Full Control
- List contents
- Read all properties
- Read permissions
- Click “OK”.
Step 3: Track Group Membership changes through Event Viewer
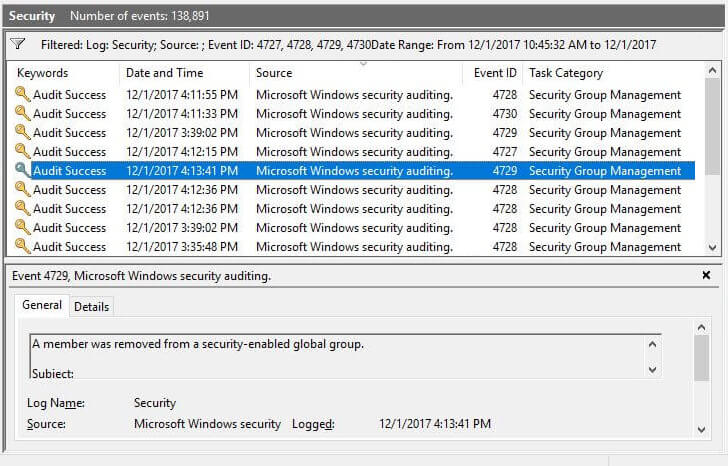
To track the changes in Active Directory, open “Windows Event Viewer,” go to “Windows logs” → “Security.” Use the “Filter Current Log” in the right pane to find relevant events.
The following are some of the events related to group membership changes.
Below screenshot indicates a Security Group is created.
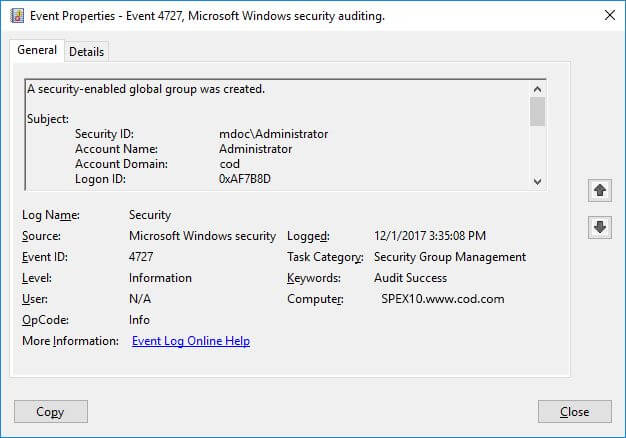
The following screenshot shows more detail of this event.
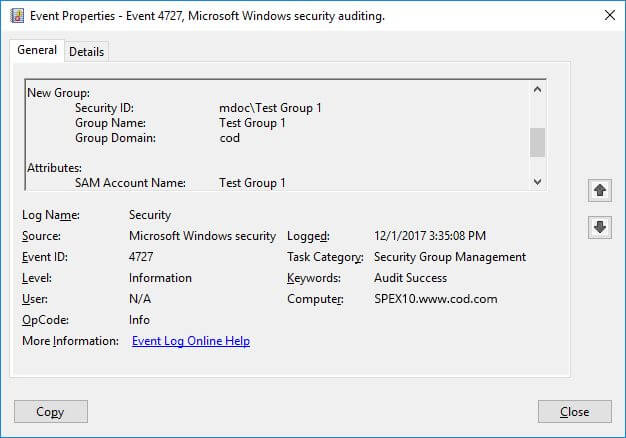
The following screenshot filters all events related to changes in Active Directory Group Memberships.
The Issues with Auditing AD Group Membership Changes Natively
Native auditing has numerous downsides, especially when it comes to Active Directory and Group Policy. Multiple events are generated for a single change, such as adding a member to a group.
Looking for a critical change in real-time is very difficult. It’s incredibly noisy, like searching for a needle in a haystack. It’s also very difficult to draw conclusions, as events lack context on their own. In many cases, relying on native auditing when auditing AD group membership changes will not be enough to ensure the security and operability of Active Directory.
Using Lepide Active Directory Auditor to Audit Group Membership Changes
Lepide Active Directory Auditor overcomes the limitations of Native Auditing with detailed, contextual, and intelligent Active Directory auditing.
Lepide displays a single event for every change made so that you get all the critical audit information you need in a single pane of glass.
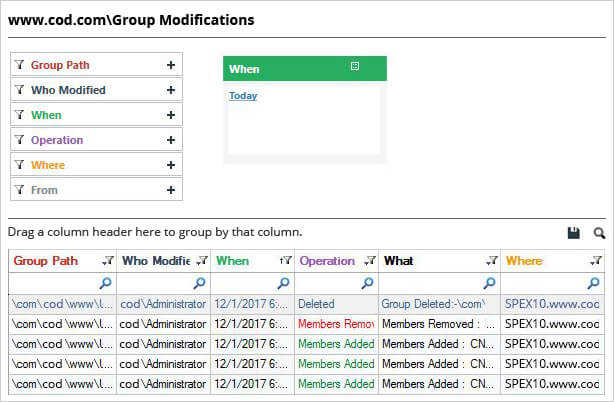
In the following image, you can see a “Group Modifications” report generated in Lepide’s Active Directory auditing solution. It shows all group membership changes made in a given period. It also shows you the answers to who, what, when, and where questions in a way that is simple to read and understand.
Using Lepide, you’ll be able to get far more visibility into the states and changes of your Active Directory. You’ll be able to determine the effective permissions of your users, see when those permissions change and see what data the users have access to. If you’d like to see this in action, and start auditing your AD group membership changes, schedule a demo with one of our engineers.

