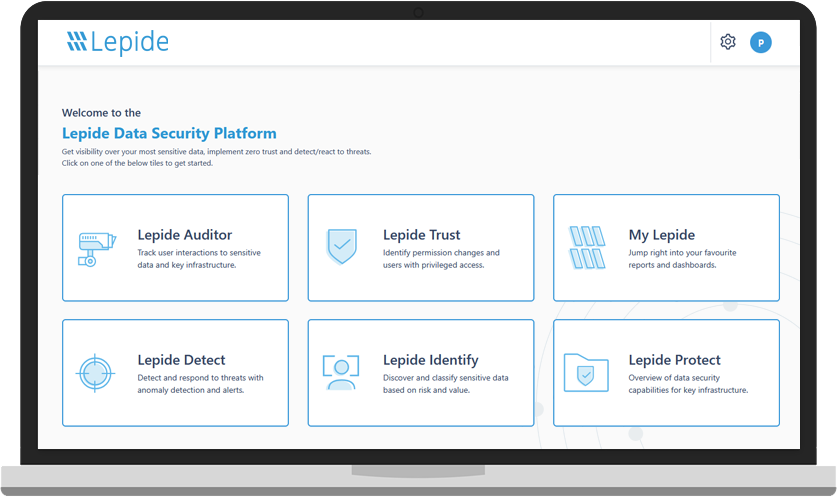
Prevent the Misuse of Student Data and Research Information
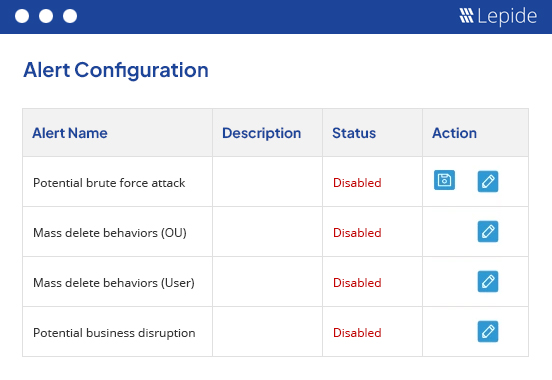
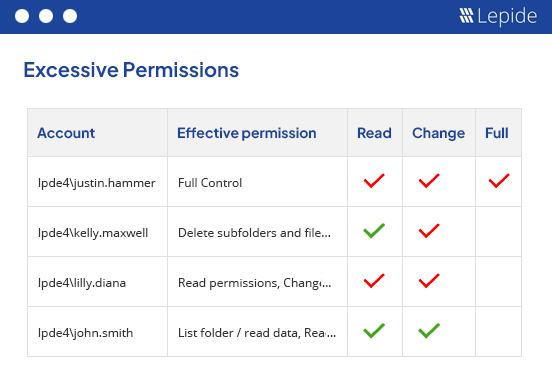
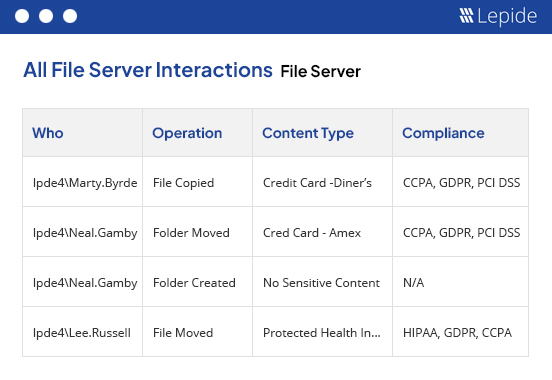
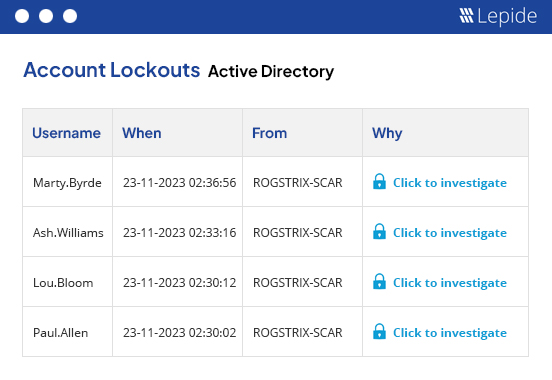
Ensure that you are safeguarding student data and research information against internal and external threats through advanced AI-backed user behavior analytics and visibility.
Fill in the rest of the form to
download the 20-day free trial
download the 20-day free trial
x