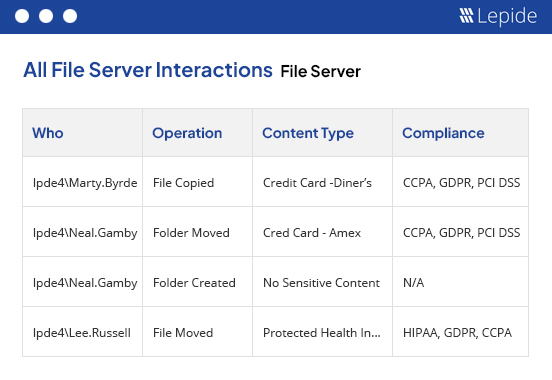
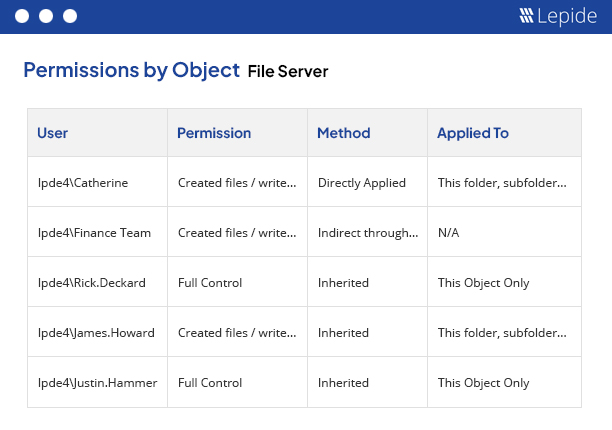
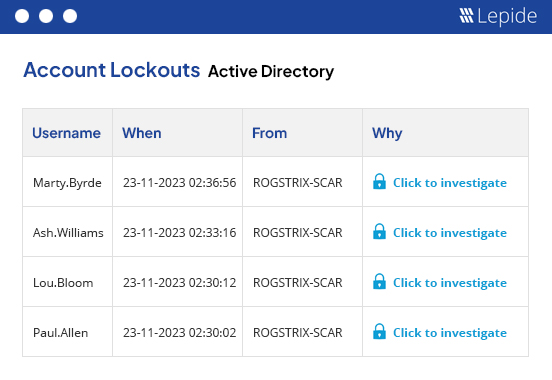
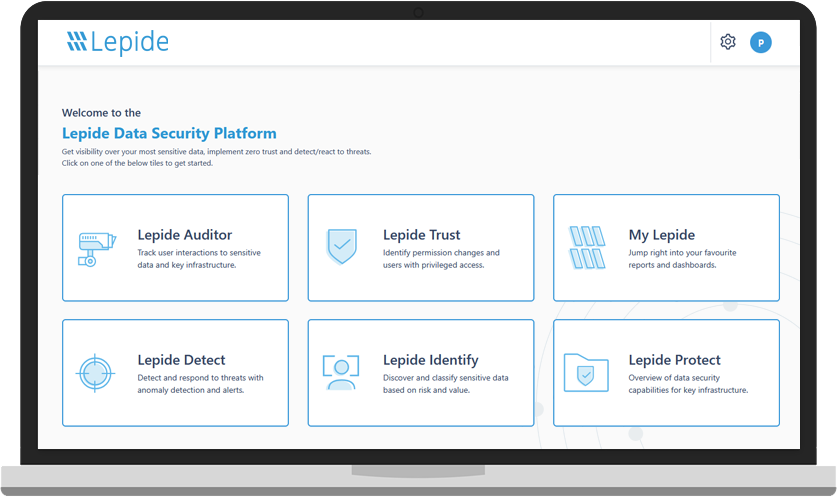
Prevent the Misuse of Financial Services Data
Protect your sensitive financial data from insider threats and external attacks through advanced user behavior analytics and visibility into critical changes.
Fill in the rest of the form to
download the 20-day free trial
download the 20-day free trial
x