Threat Detection Solution
Detect threats to Active Directory/Entra ID and sensitive, unstructured data from a single console.
Fill in the rest of the form to
download the 20-day free trial
download the 20-day free trial
x














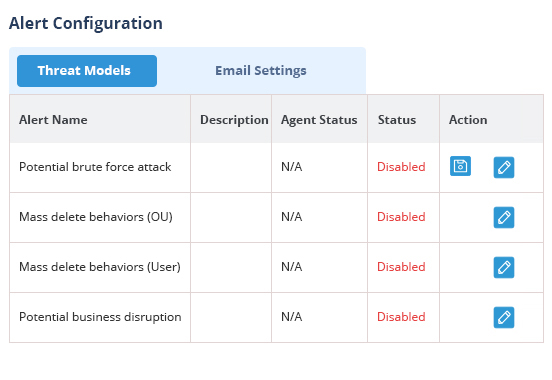
Dozens of pre-defined threat models help organizations detect ransomware, insider threats, compromised user accounts and more. Simply turn them on to start detecting threats immediately. New threat models being added with every release.
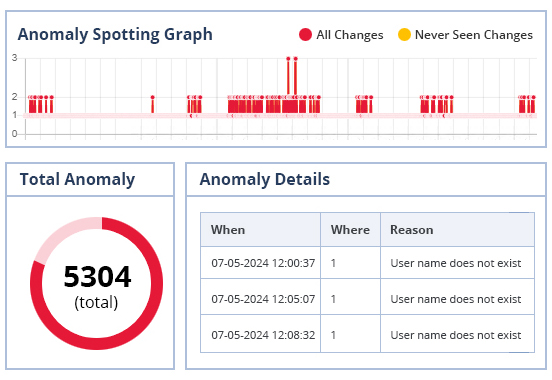
Our anomaly spotting technology learns what normal user behavior looks like over a period of time, and will then detect in real time when user behavior deviates from this norm. We can even detect single point anomalies so that you never miss a threat.
If a large number of file copy events happen in a short space of time, or hundreds of failed access attempts are taking place, these are all indications of ongoing threats. With Lepide, you can configure our threshold alerting to detect these kinds of threats.

By following the guidelines outlined in this paper, your organization can establish a robust data access governance program that supports its business objectives and protects your valuable data assets.
Get the free guide now!