Lepide Identify
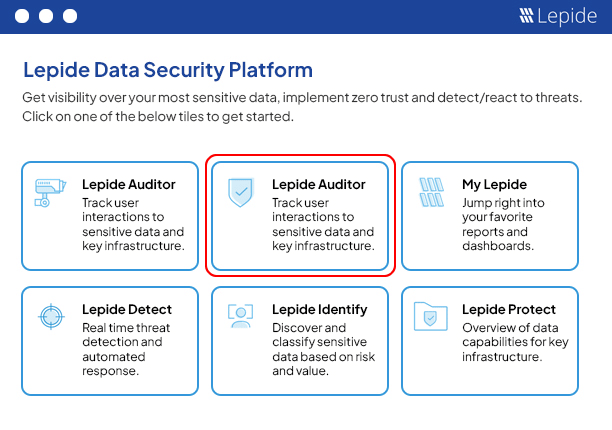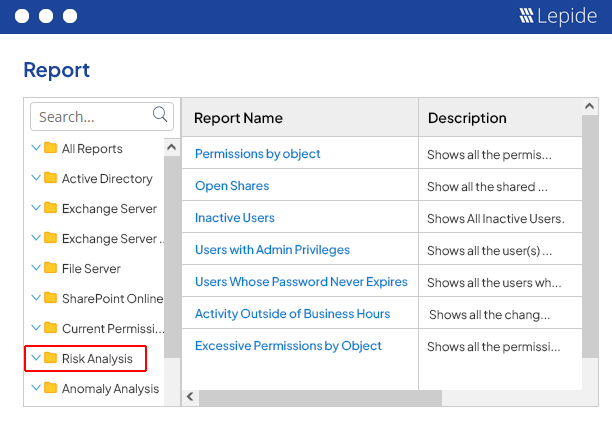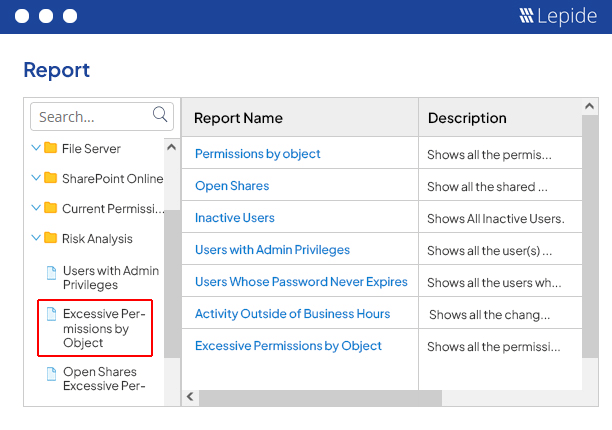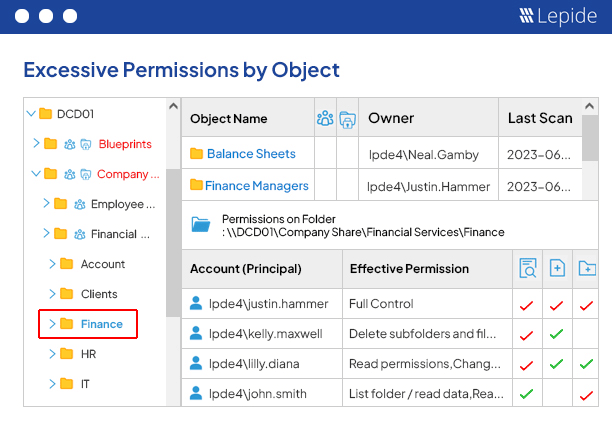
Data Discovery and Classification Software
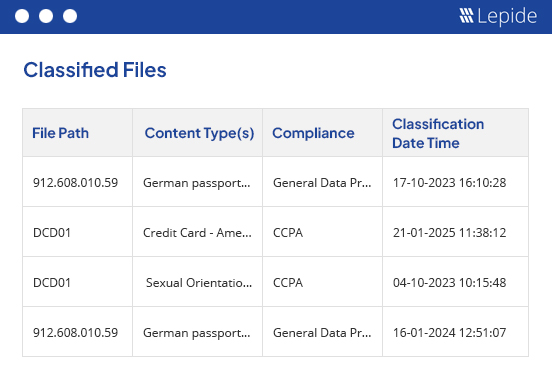
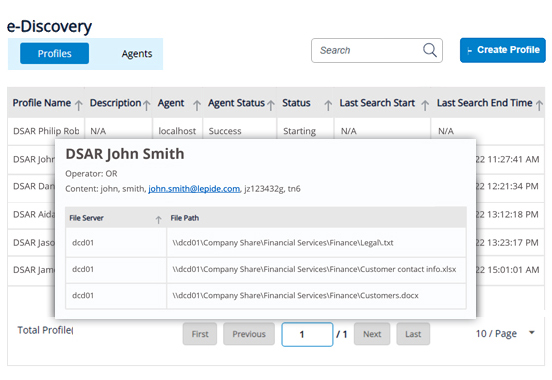
Persistent data classification adds context to your security efforts. E-Discovery helps to speed up privacy and data subject access requests.
Fill in the rest of the form to
download the 20-day free trial
download the 20-day free trial
x