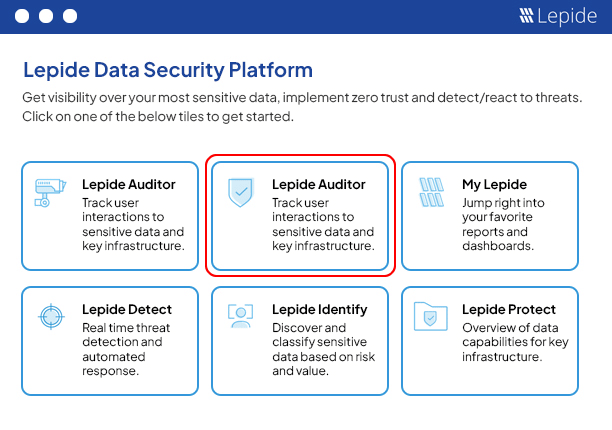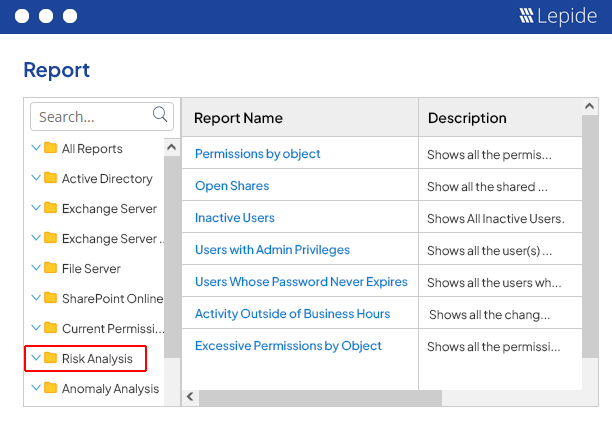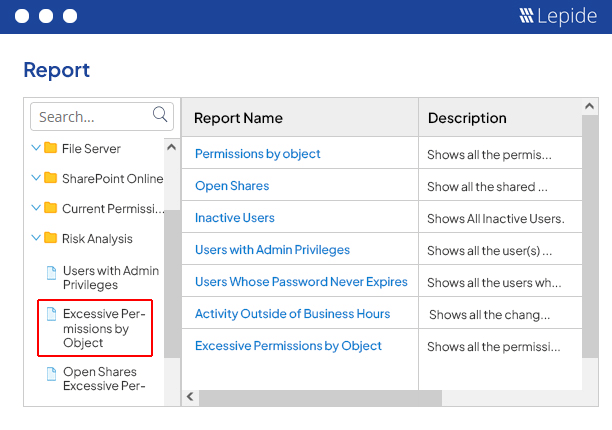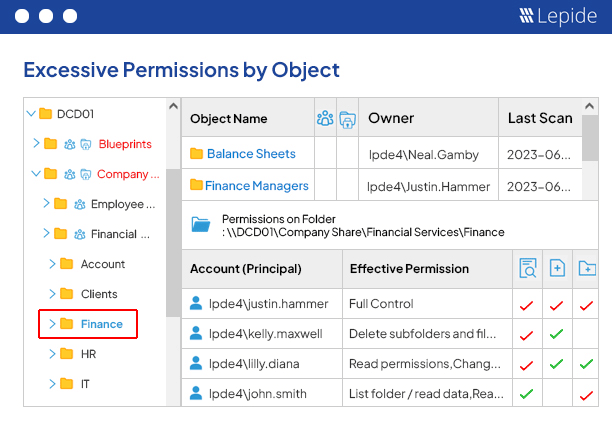
Lepide Protect
AI-Driven Permissions Management Software
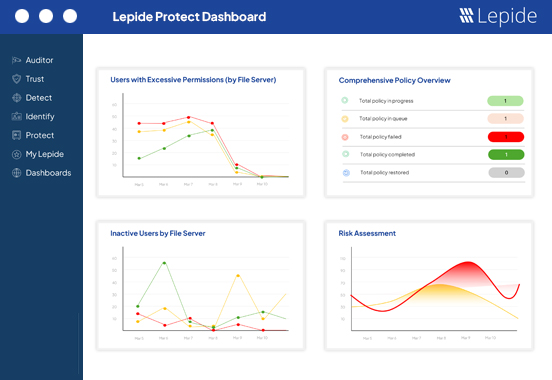
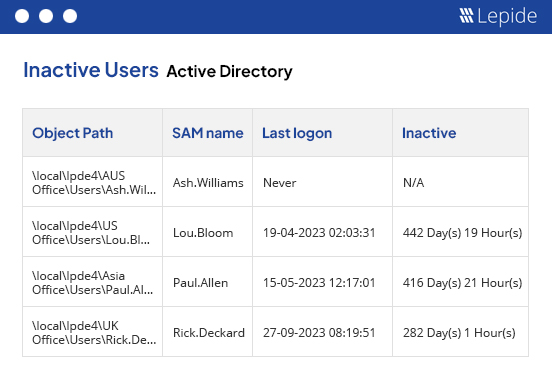
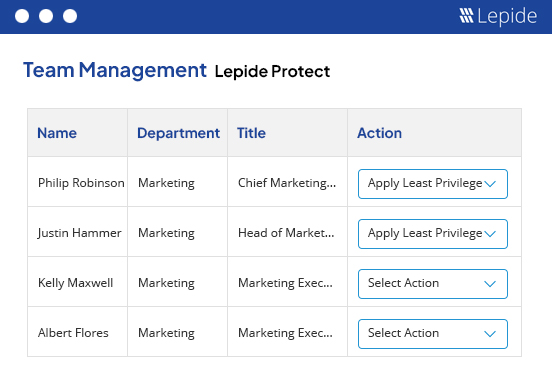
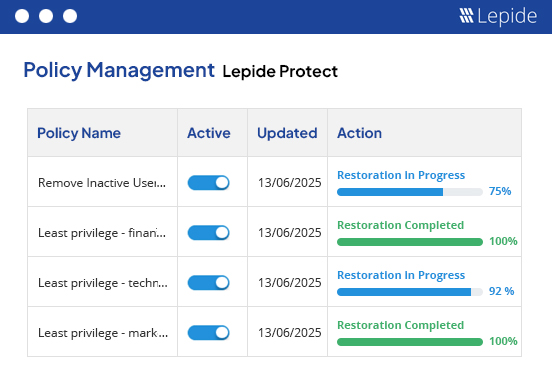
Easily define, monitor, and adjust permissions across your environments to prevent unauthorized access to sensitive information by ensuring that only authorized personnel have access to critical data.
Fill in the rest of the form to
download the 20-day free trial
download the 20-day free trial
x