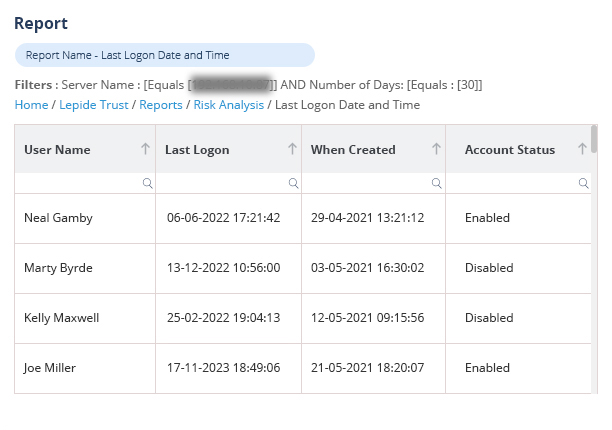
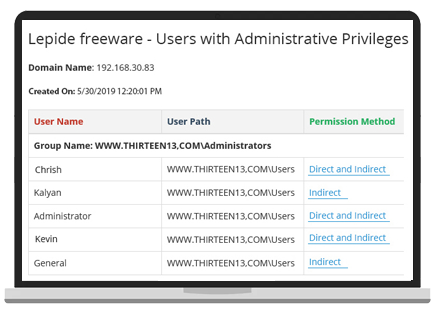
Companies should look for AD auditing tools that offer comprehensive and real-time monitoring capabilities, allowing them to track changes to user accounts, group memberships, permissions, and policies. The tool should provide detailed and easily searchable logs, customizable alerting mechanisms for critical events, and robust reporting features to meet compliance requirements. It should also offer integration with other security systems and support for long-term log retention with secure storage. User-friendly dashboards and automated analysis features can help in quickly identifying suspicious activities and potential security threats. Additionally, scalability and support for various environments (on-premises, cloud, or hybrid) are crucial to ensure the tool fits the company's current and future needs.