Dell EMC Isilon auditing with Lepide.
Lepide Auditor for Dell EMC Storage provides a scalable means of auditing changes and classifying data on Dell EMC Isilon. Get the security intelligence you need to properly protect and audit Dell EMC Isilon, including the “who, what, where, and when” of all changes made. Bolster Dell data storage security, speed up investigations, mitigate the risks of privilege abuse and meet compliance requirements.
Audit user behavior.
Spot when your users are acting suspiciously, or when accounts may have been compromised, through detailed audit reports for all file interactions; including copy events, failed reads, deletions, creations, and modifications.
Track permissions.
Get instant visibility over when permissions to files or folders change so that you can ensure only the right people have the right levels of access to your most sensitive data. Get real time alerts delivered to your inbox, or to the mobile app, so that you can keep your threat surface minimized.
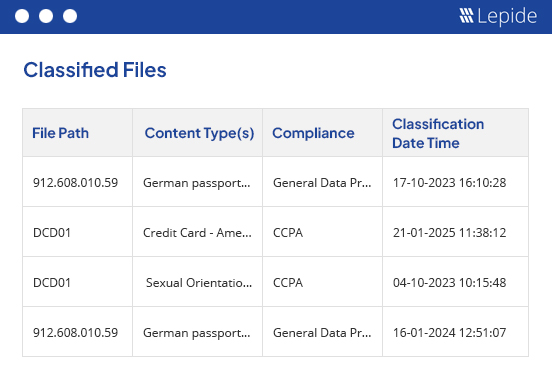
Discover & classify.
Discover and classify sensitive data created and stored within Dell EMC Isilon. Classify at the point of creation to avoid lengthy scans. Prioritize your security efforts on the data that matters most.