File Share Auditing
Get a complete overview of all changes made to shared files and folders.
Fill in the rest of the form to
download the 20-day free trial
download the 20-day free trial
x














With vast amounts of data being generated daily in all organizations, it is crucial that you identify issues such as data access attempts and unwanted modifications made to shared files and folders. Lepide File Server Auditor enables you to get a complete overview of all events taking place in your File server environment with detailed reports and real-time alerts. Our automated solution constantly monitors and tracks malicious activities which might lead to serious security breaches.
The comprehensive auditing offered by our solution provides a summarized view of accesses to the shared files and folders. You can effortlessly examine access trends across your server using our consolidated reports; containing who, what, where and when details for every single change.
Analyze changes made to the shared files and folders across your whole File Server environment using Lepide File Server Auditor. Detect malicious access or alteration of data using our granular reports with insightful and actionable details. This automated solution lets you spot anomalous event trends which helps to minimize access at unexpected or unusual times. The inbuilt filters allow you to extract in-depth information about operations like read, write or modify performed on your shared files and folders.

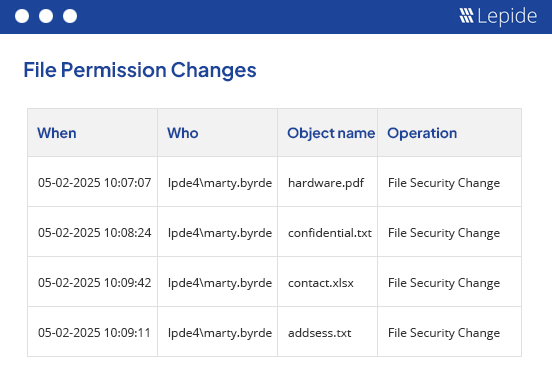
It is crucial that you recognize unauthorized modifications made to the shared files and folders in your server environment to prevent data leakages or destruction of confidential information. Lepide File Server Auditor offers consolidated reports for permission changes. Our solution enables you to spot actions that might compromise the data assets of your organization. As these reports are created for all the folders, you will have to extract the details of permission changes for shared files and folders separately.

With Lepide File Server Auditor, you can analyze the historical permissions changes of shared files and folders. You can view what permission has been applied to the selected shared file or folder and when. You can also compare the permissions of any file or folder between two specific time intervals using this report. These reports saved in PDF, MHT or CSV files.

Lepide File Server Auditor allows you to analyze the effective permissions applied on the shared files and folders with a dedicated set of reports. These reports can be easily sorted, filtered and saved for future reference. Our audit reports display the folder level where permission inheritance is broken. You can easily identify whether the effective permissions on various folders are direct, indirect or inherited.

By following the guidelines outlined in this paper, your organization can establish a robust data access governance program that supports its business objectives and protects your valuable data assets.
Get the free guide now!