Microsoft 365 Auditing Solution
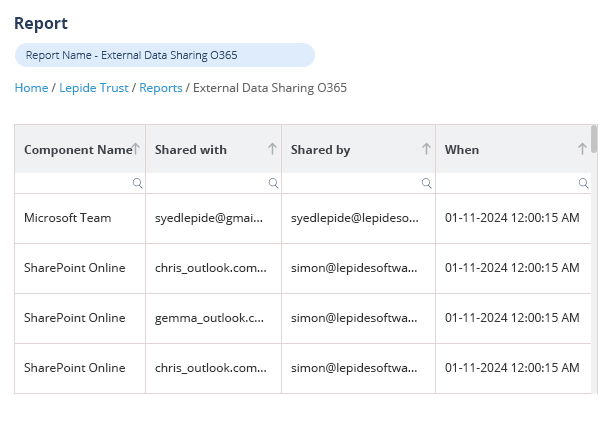
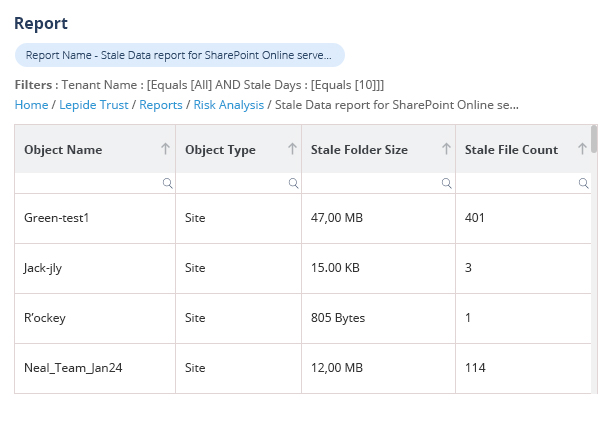
Get more visibility over how your users are accessing and interacting with your sensitive data with advanced Microsoft 365 auditing capabilities to prevent data breaches and meet compliance.
Fill in the rest of the form to
download the 20-day free trial
download the 20-day free trial
x