
- Support
- |
- sales@lepide.com
- |
- +1-800-814-0578

Netwrix relies very heavily on SQL Reporting services which has significant issues when trying to work with large datasets. Netwrix simply does not scale. Lepide scales far better, particularly in more complex environments.
Netwrix fundamental architecture is reliant on outdated technology, meaning their reports typically take twice as long to generate as Lepide. Faster reporting and alerting means faster threat detection.
While Netwrix does have the capabilities to show excessive permissions and help understand who has access to what, it is limited in comparison to Lepide. Lepide is a far more complete permissions management solution.
The below table is based on publicly availably information and feedback from our customers (including customers that have come to us directly from Netwrix).
| Functionality | Description | Lepide | Netwrix |
|---|---|---|---|
| Data discovery and classification | Locate, classify, tag, and score data based on pre-defined rule sets. | ||
| Data auditing and monitoring | Auditing states and changes across on-premises and cloud environments. | ||
| Active Directory / Entra ID security | Auditing, permissions analysis, and threat detection for AD/Azure AD. | ||
| Data access governance | Permissions analysis, permission change monitoring, and permissions remediation. | ||
| Threat detection / response | Pre-defined threat models and workflows. User behavior analytics, anomaly spotting. | ||
| Compliance reports | Predefined reports for compliance (HIPAA, GDPR, CCPA, etc.). | ||
| Scalability | How effectively does the solution perform at scale? How many resources does it require? | ||
| Performance | How fast and reliable are the reports and alerts? | ||
| Support | Quality of the ongoing support and maintenance provided. | ||
| Pricing | Total cost of ownership. |
Audit changes and interactions on a wide variety of on-premise and cloud platforms, including Active Directory, File Server, Exchange, Microsoft 365 and more. Audit how your users are interacting with your sensitive data, including moving, copying, renaming, modifying, deleting, and more. Consolidate raw log data into actionable, easy to understand reports. Access hundreds of pre-defined audit reports or customize your own reports to get the information you need.
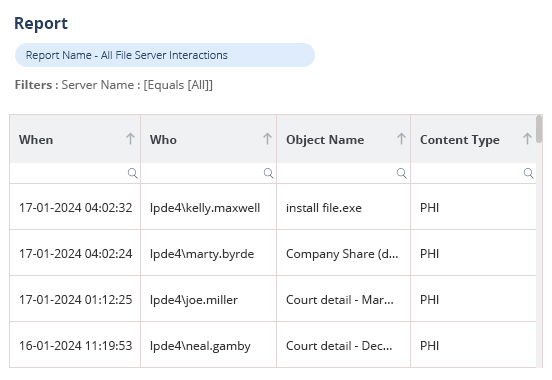
All our data classification technology has been fully developed in house and is supported by our world class internal support team. We allow you to find out where your most sensitive data is located and classify it according to sensitivity and related compliance requirements.
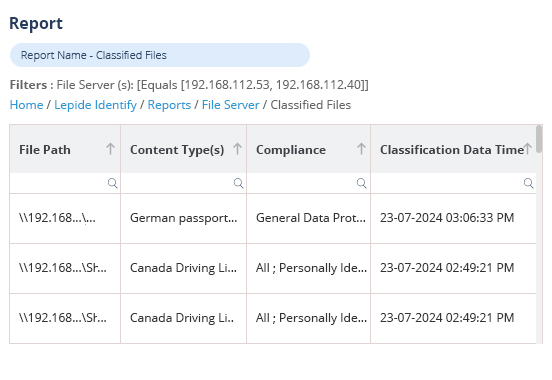
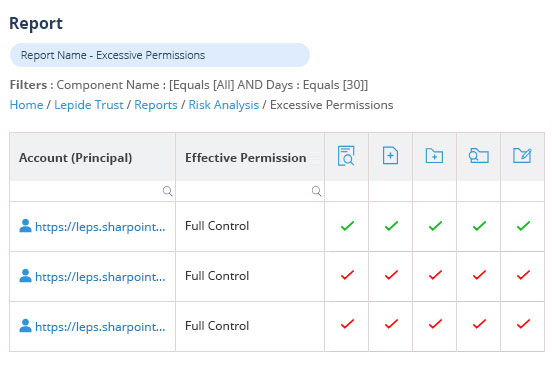
Easily determine who has access to your most sensitive data and spot excessive permissions with predefined reports. Automate least privilege where users only have access to data they need to do their job by revoking excessive permissions using automations or policies.
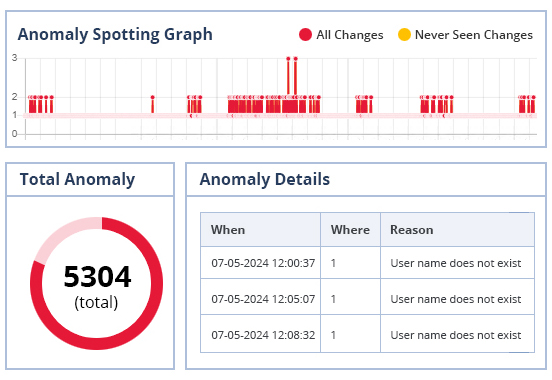
Spot anomalies in user behavior or events that could potentially indicate security breaches or attacks. Our solution can also spot changes to systems and audit security states in Active Directory, File Server and others that are indicative of a potentially insecure environment.
We have a simple and reasonable approach to pricing and licensing which means you get the full value of our solution with no nasty hidden fees. Our agent or agent-less architecture and limitless integration capabilities mean that we are one of the most scalable solutions on the market today. Our award-winning support team are on hand 24x5 to help you with all manner of inquiries.

Through our universal auditing module, which enables you to connect to any platform using a restAPI or Syslog, you can get visibility over the broadest scope of platforms on the market today. No other vendor offers the range of on-premise and cloud-based platforms that Lepide can offer, including Varonis.