The working world changed drastically in 2020. Mandated work from home orders across the world have led to a rise in organizations adopting remote working as the new norm. Security teams are concerned that maintaining proper data security will be harder with a remote workforce. It doesn’t have to be. Lepide can help you maintain data protection and compliance postures, whilst also detecting and reacting to threats – even with a remote workforce.
Know how data and resources are being used, to ensure data security and mitigate the risk of insider threats.
Keep an eye on crucial tasks, spot when users are behaving dangerously and take immediate action to mitigate threats.
Identify those workers who are taking work from home as an excuse to be lazy and kick them into gear.

Record every action of every employee as it happens, wherever they are. This tool can be quickly deployed on any endpoint or server and is incredibly lightweight.
Provides indexed, recorded footage from simple, date-stamped thumbnails for every action. Can be run with or without the user’s knowledge.
Easy to install, deploy and manage and is lightweight and secure. Helps quickly ensure security and productivity across the enterprise.

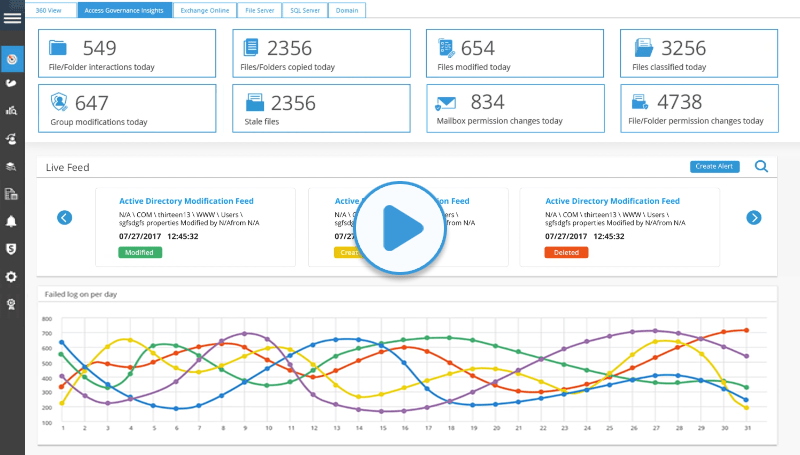
Detailed audit trail of every interaction of every user across your most sensitive data stored on any enterprise data store.
Flexible reports that show you when files are copied, modified, deleted, accessed or attempted to be accessed all of which can be automatically scheduled and delivered.
Up and running in under 30 minutes. Helps IT and security teams with their incident response, investigations and compliance reporting.
Take a virtual tour of the Lepide Data Security Platform in our web-based demo. See how Lepide aligns with your use case, whether it be ransomware, Active Directory security, Microsoft 365 security, data protection, data access governance or more.
Launch in-browser demo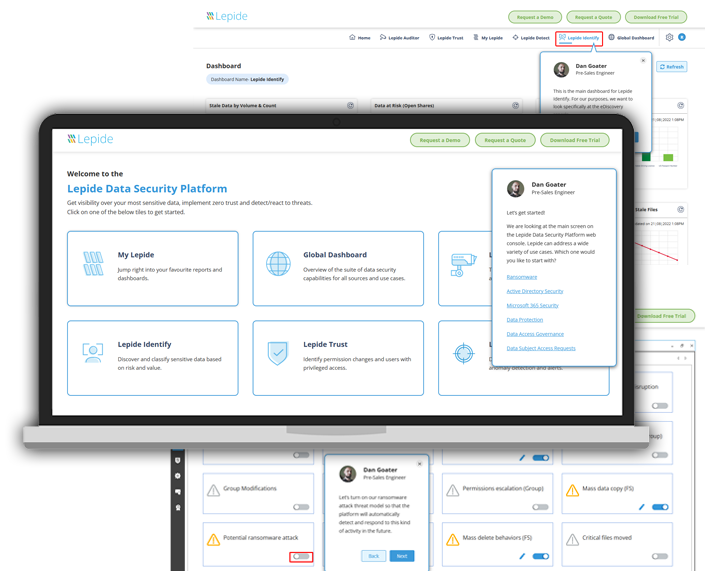

Get alerts when employees act in any way that deviates from previously learnt behavior and create threshold alerts to detect potentially suspicious activities.
Helps prevent data breaches, spot compromised user accounts, detect ransomware spread and prevent insider threats.

Discover and classify sensitive data to ensure you know where it is to take better steps to make sure it’s not over exposed.
Understand who has access to your most sensitive data by uncovering permissions to help reduce excessive permissions.
Helps in decreasing the exposure of sensitive data and ensures only those people that need access have access.

Get detailed logon and logoff reports for all active directory logon and logoffs events. Identify the exact time, location and understand the exact who, what, where and when of each event. Spot anomalies in logon/logoff times. Helps ensure productivity, increase security and meet compliance.

Enables users to reset their own active directory passwords through a secure, customizable web portal.
Employees can reset passwords either via an OTP via SMS or through answering a series of security questions. Enables enterprises to instantly resolve locked AD accounts in minutes.
Easy to deploy, ideal for enterprises with a mobile workforce and stretched IT resources.